Fast Flux is a DNS technique which involves frequent and rapid changing of the IP addresses associated with a Fully Qualified Domain Name (FQDN) by using a network of compromised hosts (Bots) acting as reverse proxies. Fast Flux Networks are commonly used by cybercriminals to distribute malware, launch phishing attacks, and facilitate other cybercrimes, posing significant challenges for cybersecurity professionals in detection and mitigation efforts.
Fast Flux Network
The core concept of a Fast Flux network involves associating multiple IP addresses with a single domain name, and then constantly swapping those IP addresses in quick succession by changing DNS A or AAAA records, using a very low TTL (Time-To-Live) value. These IP addresses belong to compromised hosts which are known as bots or fast-flux agents. Fast Flux technique is employed by the adversary (Botmaster) to evade C2 server detection and IP based Blacklisting by hiding the C2 server behind a network of compromised hosts acting as reverse proxies. Fast-Flux network ensures that a victim client will only connect to fast flux agents, but never to the real C2 server. There are two types of Fast-Flux Service Network: Single-Flux Network and Double-Flux Network.
Basics of Fast-Flux Network:
To establish a fast-flux network, the attacker initially utilizes a botnet comprising thousands of bots, all linked to the attacker’s command and control (C2) server. These participating bots, referred to as fast-flux agents, primarily serve to act as reverse proxies. Essentially, these fast-flux agents function as intermediary servers, relaying requests from clients to the C2 server and then transmitting the C2 server’s responses back to the clients.
In a fast-flux network, the attacker frequently reassigns the IP addresses linked to a Domain Name or Name Server within a very short period of time from a large pool of bots (known as fast-flux agents). The various IP addresses of the malicious domain name in a fast-flux network correspond to the IP addresses of these fast-flux agents. The Fast Flux Service Network’s technique of dynamic IP address rotation complicates the task of cybersecurity experts in tracking down and addressing malware threats.
Moreover, in a single-flux network, only the malicious Domain Name uses IP addresses from the fast-flux agents and the Authoritative Nameserver is hosted in a bulletproof hosting server. But In a double-flux network, the malicious Domain Name and the Authoritative Nameserver both use IP addresses that belong to the fast-flux agents.
Fast-Flux Mothership / C2 Server:
Fast-Flux C2 Servers are the backbone of fast-flux networks. The C2 server is a complex server which is used to control or manage the botnet and fast-flux network. The C2 server has a lot of server running on the backend to deliver various services as needed. Such as a DNS server for the malicious domain name resolution, HTTP server for delivering malware files or setting up phishing sites etc. In a fast-flux network the C2 server is also refereed as mothership server. Fast-Flux Service Network (FFSN) is not only limited to HTTP application moreover any application that uses DNS can use the Fast-Flux Service Network (FFSN).
Single-Flux Network:
Single-Flux refers to the frequent and rapid changing of IP addresses associated with a domain name. In single flux networks the DNS A or AAAA records for a domain are constantly updated with the address of fast-flux agents that act as reverse proxies.
In single flux networks, the attacker manages an Authoritative Name Server for name resolution of the malicious domain name and dynamically updates the DNS A record with the IP addresses of fast-flux agents with a very short TTL value. The Authoritative Name Server is hosted in a bulletproof hosting server.
At the expiration of TTL, new IP addresses replace the old ones for these DNS A records in the DNS Zone file. Thousands of fast-flux agent’s IP addresses are used in a cyclic order for the DNS A record. DNS A record changes as often as every 3-10 minutes, which means that the victim client connecting to the malicious domain every 3 minutes would actually be connecting to a different IP address each time.
When a victim client wants to resolve a malicious domain name, it sends the DNS query to the Recursive DNS Server. The Recursive DNS Server in turn resolves the queried domain name (FQDN) and returns a set of IP addresses back to the client. These IP addresses are actually the IP addresses of fast-flux agents which work as a reverse proxy server. The victim client then initiates connection to one of the resolved IP addresses and send its HTTP query there. The fast-flux agent at that address forwards the client request to the C2 server and deliver the content received from the C2 server back to the client. Hence, the victim client cannot communicate directly with the C2 server; instead the victim client communicates with C2 server via fast-flux agents which acts as reverse proxies.
 How does Single‐Flux Network work
How does Single‐Flux Network work
Depicted in the figure above the attacker has registered a domain name flux.com and manages an Authoritative Name Server(ns.flux.com) for the name resolution of flux.com. The Authoritative Name Server is hosted in a bulletproof hosting server. The attacker leverages a botnet to implement the fast-flux network. The botnet contains thousands of bots and all of these bots are connected with the attacker’s C2 server. In a fast-flux network, these bots are also called as fast-flux agents. The attacker’s C2 server address is c2.flux.com. The C2 server is used for malicious activity such as hosting phishing sites, delivering malware, controlling the malware-infected hosts and botnet etc.
A malware-infected client wants to connect with its C2 server at c2.flux.com. To resolve that c2.flux.com domain name, the malware-infected client sends a DNS query to the Recursive DNS Server. The Recursive DNS Server sends a DNS query to the Root Server asking for the IP address of c2.flux.com domain name. The Root Server answers with a referral IP address of the .COM Name Servers. Then the Recursive DNS Server sends DNS query to that .COM name server. The .COM name server replies with the referral IP address of Authoritative Names Server of the c2.flux.com. Finally, the Recursive DNS Server sends DNS query to the Authoritative Name Server (ns.flux.com) and gets list of IP addresses (36.10.85.230 and 215.126.9.18) for the domain name c2.flux.com. After that the Recursive DNS Server sends those resolved IP addresses to the client.
Note that, the attacker manages Authoritative Name Server (ns.flux.com) by himself and has dynamically updated DNS A record with the IP addresses 36.10.85.230 and 215.126.9.18 of fast-flux agents. Hence the Authoritative Name Server has replied IP addresses 36.10.85.230 and 215.126.9.18 of fast-flux agents as the resolved IP of c2.flux.com.
The infected client then initiates a connection with one of the resolved IP address 36.10.85.230 and sends HTTP content request to that fast-flux agent.
The fast-flux agent at that address (36.10.85.230) forwards the client request to the C2 server and deliver the content received from the C2 server back to the client. Hence, the client cannot communicate directly with the C2 server; instead the malware-infected client communicates with C2 server via fast-flux agents which acts as reverse proxies.
As we can see in the figure, the TTL (Time to Live) value is 300 seconds.
c2.flux.com. 300 IN A 36.10.85.230
c2.flux.com. 300 IN A 215.126.9.18
After TTL value expires, the attacker will dynamically update DNS A records with the new IP addresses of fast-flux agents from the botnet. That means the victim client connecting to c2.flux.com every 5 minutes would actually be connecting to a different fast-flux agent each time.
For example, 5 minutes later, the DNS A record may look like this.
c2.flux.com. 300 IN A 86.11.14.158
c2.flux.com. 300 IN A 239.4.13.123
And the infected client would connect to a fast-flux agent with an IP address of 86.11.14.158.
Double-Flux Network:
Double-flux refers to dynamically and repeatedly changing the IP addresses of both the Domain Name and its Authoritative Nameservers with a very low TTL value.
The Double-Flux process is done by changing the DNS A and DNS NS Glue record frequently in the DNS Zone file with the IP address of fast-flux agents. Thousands of fast-flux agents get involves in the process and frequently register and deregister their IP addresses as part of a DNS A record and DNS NS Glue record, for the domain name and for the authoritative name server respectively.
A glue record is the IP address (A record) of a Nameserver at the domain name registry. Glue records are required when the Nameservers for a domain name are the sub-domains of the domain name itself.
Suppose the attacker registered a domain name flux.com and its Authoritative Nameserver address is configured as ns.flux.com. The ns.flux.com Nameserver is assigned with the IP address 215.126.9.18 of a fast-flux agent and the flux.com domain is assigned with IP address 36.10.85.230 of another fast-flux agent.
flux.com. 300 IN NS ns.flux.com
ns.flux.com 300 IN A 215.126.9.18 (Glue Record)
flux.com. 300 IN A 36.10.85.230
In a double flux network, the IP address (A Record) of the ns.flux.com (Authoritative Nameserver) and also the IP address (A Record) of flux.com (Domain) changes constantly.
The different IP addresses of both the malicious Domain Name and the Authoritative Nameserver in a double-flux network are the IP addresses of fast-flux agents. The attacker uses thousands of fast-flux agents from his botnet and periodically register and deregister these IP addresses for the Domain Name and for the Authoritative Nameserver.
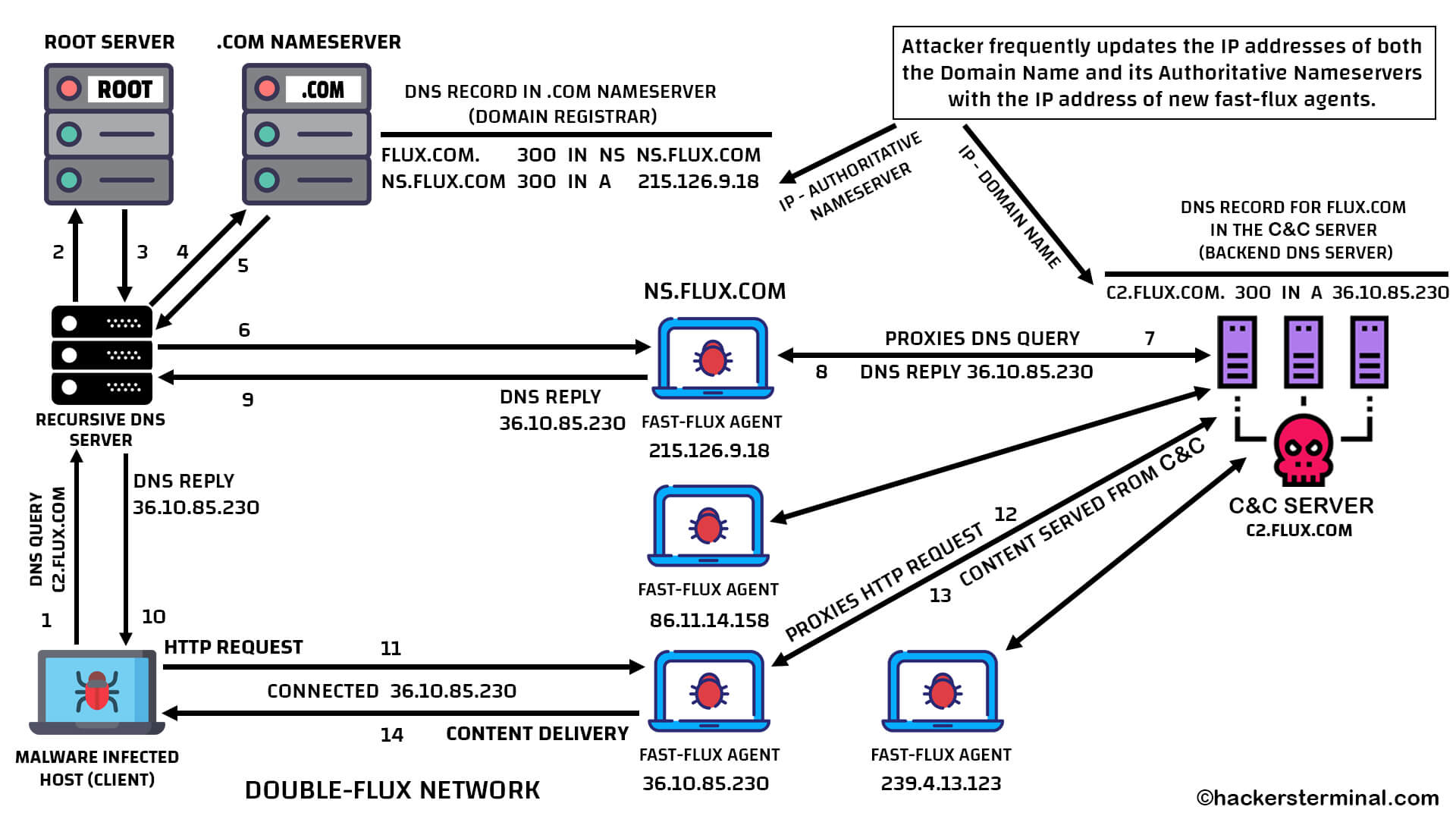
How does Double‐Flux Network work
Depicted in the figure above, the attacker registered a domain name flux.com and its Authoritative Nameserver address is configured as ns.flux.com. The attacker is using c2.flux.com domain as the web address of his C2 server.
The attacker designated a fast-flux agent with IP address of 215.126.9.18 as an Authoritative Nameserver of flux.com by adding a DNS Glue Record in the .COM Nameserver’s DNS Zone file.
DNS Record in .COM Nameserver:
flux.com. 300 IN NS ns.flux.com
ns.flux.com 300 IN A 215.126.9.18 (Glue Record)
The attacker also points another fast-flux agent with IP address of 36.10.85.230 for the domain c2.flux.com by adding a DNS A Record for the c2.flux.com in the internal DNS Server of his C2 Server.
DNS Record in C2 Server:
c2flux.com. 300 IN A 36.10.85.230
In double-flux network, the attacker frequently updates the IP addresses of both the Nameservers and the Domain Name with the IP address of new fast-flux agents. IP addresses are dynamically updated after the TTL (Time to Live) get expired. In this figure TTL value is set to 300 seconds, which is 5 minutes.
5 minutes later, the DNS Glue Record of the Nameserver will be dynamically updated with the IP address of new fast-flux agent.
flux.com. 300 IN NS ns.flux.com
ns.flux.com 300 IN A 86.11.14.158 (Glue Record)
Also 5 minutes later, the DNS A Record for the Domain Name will be dynamically updated with the IP address of new fast-flux agent.
c2flux.com. 300 IN A 239.4.13.123
How does Double‐Flux Network work:
DNS Name resolution and HTTP content retrieval process in double fast-flux network:
In a double fast-flux network when a client wants to resolve a malicious domain name, it sends the DNS query to the Recursive DNS Server. The Recursive DNS Server asks the Root Server which name server is responsible for the malicious domain and the Root Server refers to ask the .COM server. Then the Recursive DNS Server again asks the .COM Server. As the attacker configured DNS NS record pointing to fast-flux agent’s IP address on the .COM server’s DNS zone file. The .COM server replies back with the IP address of a fast-flux agent as the Authoritative Nameserver of queried malicious domain name. Now the Recursive DNS Server sends DNS query to the Authoritative Nameserver (fast-flux agent) to resolve the IP of malicious domain name.
Though the attacker designated a fast-flux agent as Authoritative Nameserver. However, the fast-flux agent does not perform any name resolution of the malicious domain. When the fast-flux agent (Authoritative Nameserver) receives a DNS query from any client, the fast-flux agent forwards that DNS query to the actual malicious DNS Server controlled by the attacker, under his C2 server. Once the malicious DNS Server answers the DNS query to that fast-flux agent then the fast-flux agent sends that answer back to the query issuer client, in this case to the Recursive DNS server. Now the Recursive DNS Server sends the resolved IP addresses of malicious domain to the actual client.
The malicious DNS Server deployed by the attacker doesn’t resolve to the IP of the C2 server or the actual web server used for hosting malicious content but instead resolve to any other fast-flux-agents IP address.
The client then establishes a connection with the resolved IP of malicious domain, which is actually the IP address of another fast-flux agent. And sends HTTP request to that fast-flux agent. Again, that fast-flux agent forwards the HTTP request to the actual Web Server running under attacker C2 server. After retrieving the content from attacker C2 server this fast-flux agent delivers the content to the client. Fast-Flux network ensures that a victim will only connect to fast flux agents, but never to the real C2 server.
In conclusion, Fast Flux Networks represent a significant challenge in cybersecurity due to their ability to rapidly change IP addresses, complicating detection and mitigation efforts. However, the complexity of cyber threats doesn’t stop with Fast Flux Networks. To gain a fuller understanding of how adversaries operate, one must also explore the concept of Domain Generation Algorithms (DGAs). These algorithms further complicate the landscape by generating numerous domain names dynamically, evading traditional security measures.