In a nutshell, Cyber Threat Intelligence (CTI) is the information that is collected, relevant, fully contextualized, filtered and analyzed to answer core questions regarding any cyber threats that an organization can face, such as who is likely to attack what assets, where, when, how and why.
Cyber Threat Intelligence (CTI)
Cyber Threat Intelligence (CTI) is the precise and contextualized information about emerging or existing cyber threats that have been refined and analyzed to provide actionable advice which allows the organizations to take informed decision to proactively defend or mitigate any cyber threats. Cyber Threat Intelligence (CTI) provides valuable knowledge with context about the adversaries and their motivations, capabilities, goals, including the tools and methods that adversaries use to conduct cyber-attacks.
It’s important to understand that just information alone is not intelligence. Rather, information serves as the foundational raw material from which intelligence is derived through meticulous analysis. The creation of intelligence involves a detailed process that includes the collection, processing, and analysis of data. The key distinction between mere information and genuine intelligence lies in the depth of analysis involved.
Why Cyber Threat Intelligence (CTI) is Important?
Cyber threat intelligence (CTI) plays a critical role in the proactive defense of digital assets by providing organizations with the necessary insights to understand and anticipate the tactics, techniques, and procedures (TTPs) employed by cyber adversaries. It enables a more informed and effective response to threats by facilitating the identification of potential vulnerabilities, improving the speed and accuracy of threat detection, and guiding the development of strategic defenses tailored to counter specific threats. By leveraging CTI, organizations can shift from a reactive security posture to a more proactive one, significantly reducing the risk of successful cyberattacks. This strategic approach not only enhances the resilience of an organization’s cyber infrastructure but also supports compliance with regulatory requirements and industry standards, further safeguarding sensitive data and critical systems. In essence, cyber threat intelligence is indispensable for maintaining a robust cybersecurity posture in an ever-evolving threat landscape.
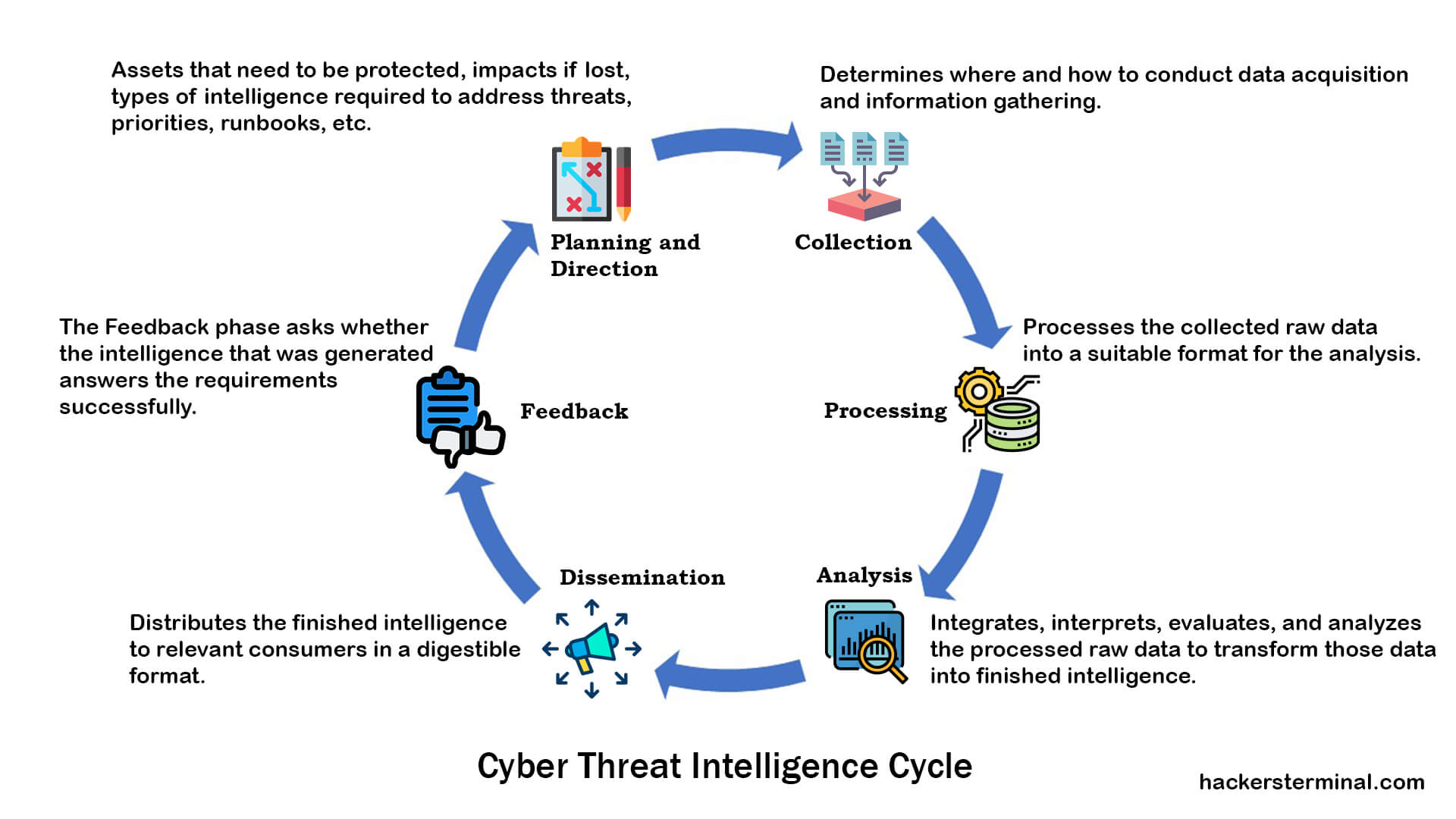
Cyber Threat Intelligence (CTI) Lifecycle Process:
Cyber Threat intelligence cycle is an iterative and adaptable process by which raw data and information is identified, collected, and then developed into finished intelligence. The traditional intelligence cycle focuses on six distinct phases.
1. Planning and Direction.
2. Collection.
3. Processing.
4. Analysis.
5. Dissemination.
6. Feedback.

Planning and Direction:
Planning and Direction involve management of the entire cyber threat intelligence operation. This phase defines the purposes and objectives of the cyber threat intelligence program. In this phase, the CTI team identifies what issues need to be addressed to protect the organization and what information must be gathered to produce threat intelligence products that satisfy the organization’s requirements.
The Planning and Direction phase determines the exact requirements of consumers (organization) through Intelligence Requirements (IRs) or Priority Intelligence Requirements (PIRs) and ensures that those requirements are met to deliver the cyber threat intelligence product to the organization as they needed. From these IRs and PIRs, the CTI team determines what data and information are required and how those should be collected.
The planning and direction phase establishes the question that cyber threat intelligence is meant to answer. These questions are given to the CTI team in the name of Intelligence Requirements (IRs) by the organization’s decision-makers or head of the cybersecurity program such as CISO (Chief Information Security Officer). Intelligence Requirements (IRs) is the request of what information an organization needs from a CTI team through cyber threat intelligence operation.
For example, an Intelligence Requirement (IR) could be “Which types of adversaries are deploying attacks in our organization, and what are their motivations?” This question will lead to further collections effort and help guide CTI analyst to the answers. Answering intelligence requirements requires data collection, analysis and reporting and feedback. In the planning and direction phase, the CTI analyst develops a collection management framework. This collection plan maps all sources (both internal and external) of intelligence collection to ensure they can provide the data to answer the intelligence requirements.
Three key fundamentals of the Planning and Direction phase:
3. Collection Management Framework.
Collection:
The collection phase of cyber threat intelligence involves collecting the necessary data from various sources that will likely satisfy the intelligence requirements. This phase is the execution of the collection plan determined during the planning and direction phase. The data can be collected from a large variety of sources, including internal sources and external sources. Internal data sources are typically any generated logs from organizational hardware and software regarding device usage. The internal source may include indicators of compromise (IOC), network event logs, firewall logs, router logs, IDS, records of past incident responses, vulnerability scans, etc.
The external sources include threat data feeds, code repositories, malware analysis, dark web, hacking forum, social media, paste sites, human intelligence, information sharing platforms, etc. After accumulating data from these sources, the cyber threat intelligence team would then process those data and make them ready for analysis.
Processing:
The processing phase of the cyber threat intelligence involves processing the collected raw data into a suitable format for the analysis. Collected data is not usable in the format in which it was collected as it comes from different sources with a variety of formats like XML, JSON, CSV, even plain text. Hence, the raw data is processed and converted into a uniform file format. Finally, the data is sorted, organized, filtered, and then prepared for analysis.
Here are some of the most common ways to process data related to cyber threat intelligence:
• Normalization (Normalizing collected data into uniform formats.)
• Indexing (Make searchable data list.)
• Translation (Translating the data as it may be collected from foreign sources.)
• Enrichment (Providing additional metadata and context in the data.)
• Filtering (Filtering for false and redundant information.)
• Prioritization (Data prioritization.)
• Visualization (Visualization of sorted and organized data based on what analysts need.)
Analysis:
The analysis phase of cyber threat intelligence is very crucial. The analysis phase involves integrating, interpreting, evaluating, and analyzing the processed raw data to transform those data into finished intelligence. The goal of the analysis phase is to develop a finished cyber threat intelligence product that answers the intelligence requirements (IRs) outlined in the planning and direction phase.
In the analysis phase, the CTI analyst synthesizes disparate pieces of processed data and interprets those data to identify patterns, uncover threats, determines its meaning, and enrich data with contextual information. Besides, the data is evaluated through various analytical techniques to assess the importance and implications of processed data. Tactical analysis answers what/where/when/how questions regarding threats, attacks, vulnerabilities, etc. outlined in the intelligence requirements by analyzing technical telemetry data such as network activity, malware samples, hash values, malicious domains, IPs, logs. Operational analysis analyzes specific threats, campaigns, adversaries, and their capabilities (TTP) to answer who is behind the threats, why, and how. Strategic analysis holistically assesses threats, risks, emerging technologies, and geopolitics that may impact/provide opportunities for the organization now and in the future. Strategic Analysis answers who is attacking and why?
Cognitive biases, perceptual biases, and reasoning errors can cause inaccurate evaluation. Therefore Structured Analytic Techniques (SATs) are leveraged to reduce biases. Through integration, evaluation, and analysis, CTI analyst produces the final intelligence products on time. Finished intelligence provides actionable advice regarding Intelligence Requirements (IRs) questions like what is happening, why it is happening, what might occur next, adversaries TTP (Tactics, Techniques, and Procedures), motivations, goals, etc.
The output of the analysis phase should enable action, whether that action is updating a threat profile, patching systems, or creating rules for threat detection. Actionable threat intelligence should be timely, accurate, contextual, and coherent. An interplay between collection and analysis often occurs, when cyber threat intelligence analyst realizes that the collected data is not providing the required raw material and perhaps different data needs to be collected for the appropriate analysis.
Dissemination:
The dissemination phase of cyber threat intelligence involves distributing the finished intelligence products to relevant consumers in a digestible format. The dissemination phase ensures the delivery of different intelligence reports for strategic, operational, tactical levels. These wide-ranging consumers need to be able to understand the intelligence information, digest its content, and understand what action needs to be taken. Dissemination enables organizations to operationalize intelligence work. Dissemination also determines how often intelligence reports should be distributed and with what format etc. Proper dissemination of actionable threat intelligence provides the most value and applicability to intelligence consumers.
Feedback:
The feedback phase of cyber threat intelligence involves getting feedback on the finished intelligence from the intelligence consumers. The feedback determines whether the produced intelligence successfully answers the intelligence requirements or not. Depending on the feedback, the intelligence cycle may start from the beginning until the intelligence satisfies the requirements. However, the intelligence cycle will be over if the intelligence process satisfies the requirements. If the intelligence process fails to answer the requirements, then adjustments need to be made for future iterations of the intelligence distribution.
Cyber Threat Intelligence Tools:
Cyber Threat Intelligence tools are specialized software solutions designed to gather, analyze, and interpret information regarding potential or current attacks that threaten the security of an organization or its assets. These tools not only focus on identifying threats but also provide insights into the tactics, techniques, and procedures (TTPs) used by cyber adversaries. By leveraging a mix of automated and manual analysis techniques, CTI tools can sift through vast amounts of data from various sources, including open web, dark web, and internal systems, to identify indicators of compromise (IOCs) and advise on mitigating strategies.
Threat Intelligence Platforms (TIPs)
TIPs serve as the cornerstone for CTI operations by aggregating, correlating, and analyzing threat data from multiple sources in real-time. These platforms provide a centralized repository for intelligence data, facilitating the efficient management of threat indicators, such as IP addresses, URLs, and malware hashes. Tools like Anomali ThreatStream, ThreatConnect, and MISP (Malware Information Sharing Platform & Threat Sharing) are examples of TIPs that offer advanced functionalities like integration with existing security tools, threat analysis, and sharing capabilities with peers and industry groups.
SIEM Systems
Security Information and Event Management (SIEM) systems are essential for monitoring an organization’s security posture, collecting logs and data streams from various sources within the IT infrastructure. SIEM systems like Splunk, IBM QRadar, and LogRhythm provide real-time analysis of security alerts generated by applications and network hardware. They play a critical role in CTI by aggregating data that can be used to identify patterns indicative of cyber threats, thereby enhancing incident response and forensic analysis.
Open-Source Intelligence (OSINT) Tools
OSINT tools are invaluable for gathering information from publicly available sources to support CTI efforts. Tools such as Shodan, a search engine for internet-connected devices, and Maltego, a tool for graphical link analysis, help cybersecurity professionals uncover potential vulnerabilities and threats. These tools enable the exploration of the digital footprint of an organization on the internet, providing insights into exposed assets and potential attack vectors.
Vulnerability Intelligence and Management Tools
To proactively mitigate threats, organizations must be aware of vulnerabilities within their systems and applications. Vulnerability intelligence and management tools like Tenable Nessus, Qualys, and Rapid7 InsightVM offer capabilities to scan networks and systems for vulnerabilities, assess their severity, and prioritize remediation efforts. These tools are crucial for maintaining an up-to-date understanding of the threat landscape related to software vulnerabilities and misconfigurations.
Cyber Threat Intelligence Feeds
CTI feeds provide real-time data on threats, including indicators of compromise (IoCs), tactics, techniques, and procedures (TTPs) of threat actors. Subscribing to reputable CTI feeds from organizations like FS-ISAC for the financial sector, or using feeds provided by cybersecurity firms like CrowdStrike and FireEye, enriches an organization’s threat intelligence database. This information aids in the early detection of threats and accelerates the response to incidents.
Incident Response and Forensics Tools
In the aftermath of a security incident, incident response and forensics tools play a pivotal role in understanding the attack and preventing future occurrences. Tools like The Sleuth Kit (TSK) for digital forensics, and GRR Rapid Response for live incident response, enable cybersecurity teams to dissect attacks, understand the behavior of adversaries, and strengthen defenses accordingly.
For organizations aiming to establish or enhance their Cyber Threat Intelligence operations, choosing the right mix of tools is pivotal. These tools not only enable the efficient collection and analysis of threat data but also foster a proactive cybersecurity posture. By integrating these tools into their cybersecurity framework, professionals can ensure a well-rounded and effective defense mechanism against the ever-evolving landscape of cyber threats. It’s also crucial for organizations to continuously update their CTI practices and tools to keep pace with the advancements in cyber threats and technologies.
Conclusion
In conclusion, understanding cyber threat intelligence is crucial for cybersecurity professionals. CTI empowers organizations to make informed decisions about their security practices, moving from a reactive to a proactive stance in the fight against cyber threats. By learning to effectively gather, analyze, and act upon threat intelligence, cybersecurity professionals can better protect their organizations from cyberattacks. In today’s interconnected world, where threats constantly evolve, mastering cyber threat intelligence is not just beneficial—it’s essential for staying ahead of cyber adversaries and keeping sensitive data safe.
References:
1. Katie Nickels, 2019, The Cycle of Cyber Threat Intelligence Webcast, SANS Institute.
2. Jared Ettinger, 2019, Cyber Intelligence Tradecraft Report: The State of Cyber Intelligence Practices in the United States, Carnegie Mellon University.
3. Scott J. Roberts & Rebekah Brown, 2017, Intelligence-Driven Incident Response: Outwitting the Adversary, O’Reilly Media.
4. Chris Pace, Andrei Barysevich, Levi Gundert, Allan Liska, Maggie McDaniel, John Wetzel, 2018, The Threat Intelligence Handbook: A Practical Guide for Security Teams to Unlocking the Power of Intelligence, CyberEdge Group.
5. The Recorded Future Team, 2020, What the 6 Phases of the Threat Intelligence Lifecycle Mean for Your Team, Recorded Future.
6. Wilson Bautista, 2018, Practical Cyber Intelligence, Packt Publishing.
7. Anomali, 2020, What is Threat Intelligence?, https://www.anomali.com/resources/what-is-threat-intelligence
8. CBEST, 2016, CBEST Intelligence-Led Testing Understanding Cyber Threat Intelligence Operations, Bank of England.
9. Josh Lefkowitz, 2019, Why All Security Disciplines Should Use the Intelligence Cycle, securityweek.com