Event Tracing for Windows (ETW): The Ultimate Guid...
Posted by Shateel A. Chowdhury | Oct 25, 2025 | Ethical Hacking | 0 |
What is mshta.exe? How Attackers Abuse the Mshta L...
Posted by Shateel A. Chowdhury | Oct 16, 2025 | Ethical Hacking | 0 |
Fileless LotL Attacks: How mshta.exe Executes Powe...
Posted by Shateel A. Chowdhury | Oct 6, 2025 | Ethical Hacking | 0 |
Living off the Land (LotL): Fileless PowerShell At...
Posted by Shateel A. Chowdhury | Oct 4, 2025 | Ethical Hacking | 0 |
Sysmon Explained: Setup, Configuration, and Log Fo...
Posted by Shateel A. Chowdhury | Sep 10, 2025 | Ethical Hacking | 0 |
Hacker's News
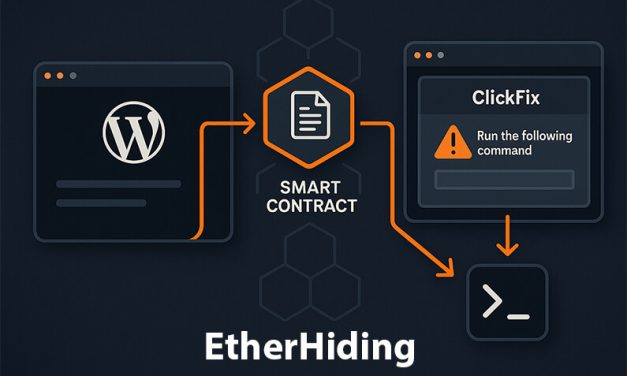
LatestUNC5142’s “EtherHiding”: Threat Actors Weaponize Smart Contracts to Deliver Malware via Hacked WordPress Sites
by Shateel A. Chowdhury | Oct 18, 2025 | Hacker's News | 0 |
TL;DR: A financially motivated group tracked as UNC5142 is hijacking vulnerable WordPress sites...

Malware Hunter – Detects Command and Control (C&C) Server!
by Shateel A. Chowdhury | Jul 16, 2017 | Hacker's News | 0 |
Ethical Hacking
LatestParent PID Spoofing: How to Detect with ETW & SilkETW
by Shateel A. Chowdhury | Nov 3, 2025 | Ethical Hacking | 0 |
Detecting Strange Parent-Child Relationships (Parent PID Spoofing) with ETW and SilkETW Parent PID...

Event Tracing for Windows (ETW): The Ultimate Guide for SOC Analysts
by Shateel A. Chowdhury | Oct 25, 2025 | Ethical Hacking | 0 |



Parent PID Spoofing: How to Detect with ETW & SilkETW
by Shateel A. Chowdhury | Nov 3, 2025 | Ethical Hacking | 0 |
Detecting Strange Parent-Child Relationships (Parent PID Spoofing) with ETW and SilkETW Parent PID...
Read MoreEvent Tracing for Windows (ETW): The Ultimate Guide for SOC Analysts
by Shateel A. Chowdhury | Oct 25, 2025 | Ethical Hacking | 0 |
What Is Event Tracing for Windows (ETW)? Event Tracing for Windows (ETW) is a powerful, built-in...
Read MoreUNC5142’s “EtherHiding”: Threat Actors Weaponize Smart Contracts to Deliver Malware via Hacked WordPress Sites
by Shateel A. Chowdhury | Oct 18, 2025 | Hacker's News | 0 |
TL;DR: A financially motivated group tracked as UNC5142 is hijacking vulnerable WordPress sites...
Read MoreWhat is mshta.exe? How Attackers Abuse the Mshta LOLBin for Fileless Attacks
by Shateel A. Chowdhury | Oct 16, 2025 | Ethical Hacking | 0 |
In the world of cybersecurity, attackers are constantly evolving their techniques to evade...
Read MoreFileless LotL Attacks: How mshta.exe Executes PowerShell Commands via Inline JavaScript
by Shateel A. Chowdhury | Oct 6, 2025 | Ethical Hacking | 0 |
Fileless attacks exploit trusted system binaries and execute payloads entirely in memory. One...
Read MoreFollow Us
Recent Posts
Recent Reviews
-
How to Install Kali Linux on a USB Flash Drive – Creating A Portable and Standalone Kali Bootable USBScore: 90%
-
DOMAIN GENERATION ALGORITHM – DGA IN MALWAREScore: 99%
-
Fast-Flux Networks in Cybersecurity: A Technique Used to Hide C2 Server IP AddressesScore: 90%
-
Cyber Threat Intelligence (CTI): Definitive Guide for BeginnersScore: 85%
Subscribe
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.















Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.
You have Successfully Subscribed!