DNS tunneling is a technique which exploits DNS protocol for tunneling data via DNS query and response packet. DNS tunneling is often leveraged as a covert communication channel for botnets and malware’s command and control (C&C) operations, enabling attackers to exfiltrate data and issue commands undetected by bypassing traditional security measures. DNS tunneling involves a method where compromised machines, infected with malware, are equipped to run a DNS Tunneling client program. Concurrently, the attacker operates a DNS Tunneling server program on their authoritative DNS server, which often serves as a command-and-control (C&C) server. In this setup, the DNS client program transmits data encoded within the hostname label of a DNS query, while the server responds with data encoded in the Resource Record (RR) of the DNS response packet. DNS tunneling can be utilized for various purposes, including communication with a C&C server, data exfiltration, and the tunneling of any Internet Protocol (IP) traffic through the DNS protocol.
DNS Tunneling Explained
The DNS Tunneling program (or malware) encodes payload data using the base64 encoding scheme within DNS query packets and then sends this data as a DNS query to the server. The Payload data is prepended as the hostname of a DNS Query. The server responds to the query with its own base64 encoded payload data in the DNS response packet, utilizing the RDATA field of various DNS Resource Record (RR) types. TXT, NULL, and CNAME records are the types most commonly used in DNS tunneling.
For example:
If the attacker registers the domain example.com then data can be transmitted as a DNS request to <base64_encoded_data>.example.com
- The client computer could send an A record query where the data is encoded within the hostname.
DNS Query: gewsSqJhs7AopOS34f32fgqqe.example.com
- Then the server could send any command/data by responding to the A query with a CNAME record as response.
DNS Response: ZwsAq5sT43jgcDkhuH6rsp.example.com
In the context of DNS tunneling, the attacker registers a domain name, such as example.com, and points its nameserver records to the server that hosts the DNS tunneling program. This server functions as the authoritative nameserver for the domain and its subdomains, enabling server-side tunneling and decapsulating the payload data by running DNS tunnel server daemon on the server.
DNS Tunneling as a Covert Channel in Botnet
The botnet’s command and control (C&C) communication channel enables the bots and their C&C server to communicate. To use DNS Tunneling as a covert communication channel, the attacker embeds DNS Tunneling methods into the malware’s code and embeds the domain name of the C&C server directly into the malware. To establish connection with the C&C server, the bot would send DNS query to resolve the IP address of C&C server.
Data Exfiltration via DNS Tunneling:
On the compromised machine (Bots) DNS tunneling client program (malware) read the data to be exfiltrated line by line. Slices the data into small chunks and performs base64 encoding on each line. Then encapsulates the base64 encoded data as subdomain labels suffixed with the attacker’s domain name in a DNS query and sends that query to the Recursive DNS Server. The Recursive DNS Server, Root, and TLD Servers process the DNS query, by locating the name server authoritative for attacker’s registered domain name and directing the “DNS query” to that server. When the DNS query with payload data arrives on to the authoritative DNS server of the attacker’s registered domain, the attacker can track down those DNS queries logs, parse them and decode the base64 encoded labels (subdomains) to reassemble the stolen data from the client (Infected bot). Then the server sends back DNS Response to the client containing new command encoded into Resource Record (RR) in DNS Response packet. That’s how data is transmitted back and forth using DNS Tunnel. DNS responses have low TTL value to avoid caching. DNS protocol does not allow the server to initiate a connection with the client; the client needs to periodically send query to pull new command from the attacker’s DNS server (C&C Server).
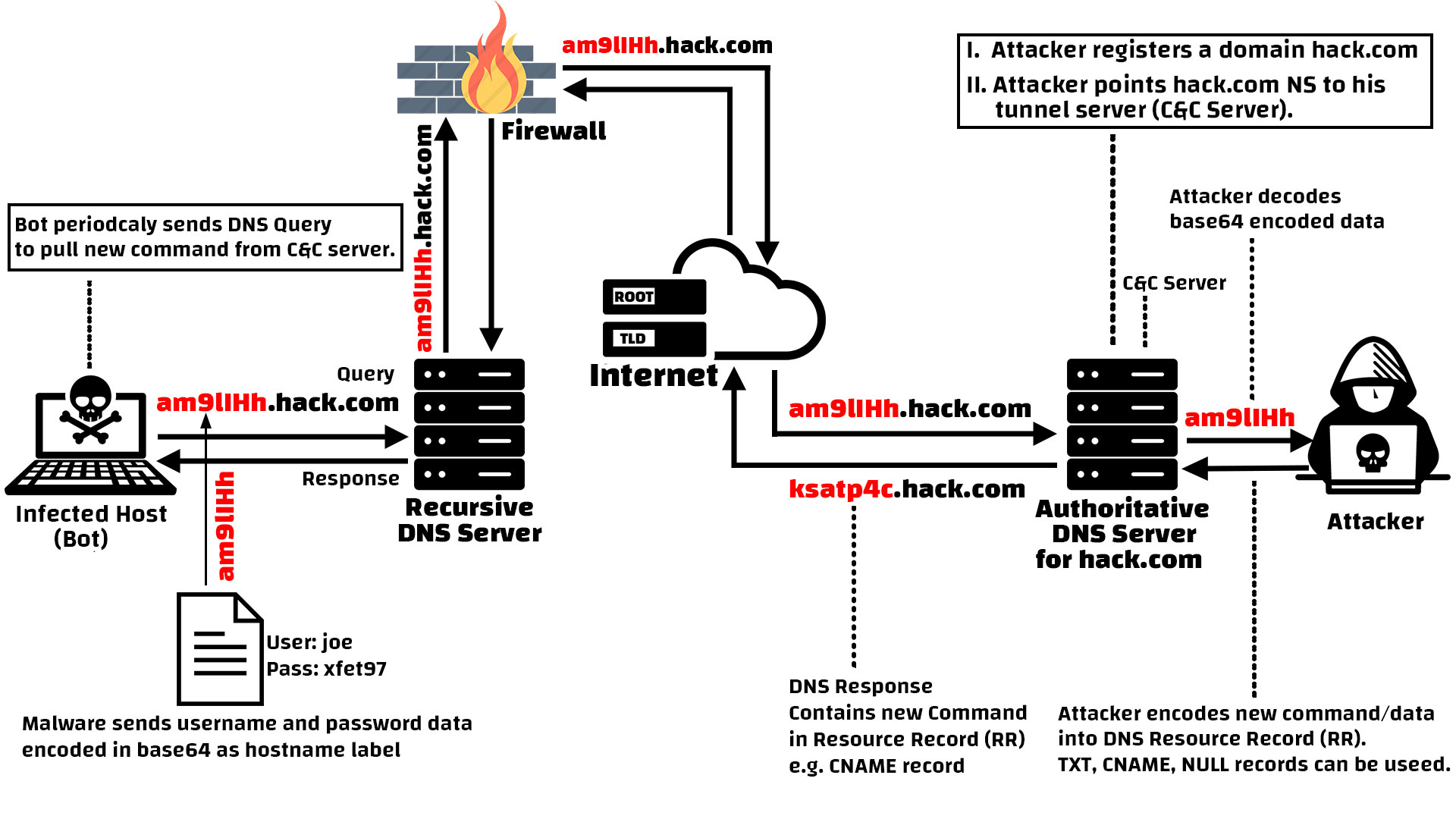
Fig: Tunneling Data and Commands Over DNS
Refer to the illustrated figure above; The attacker infects a user computer of an organization with a malicious malware. The organization has a Firewall to monitor and block malicious traffic. Web browsing and most other communication from local computers to the Internet relies on the DNS service. For that reason restricting the DNS communication can cause disruption of legitimate connectivity. Therefore DNS protocol is always allowed to outbound/inbound in Firewall. And attacker takes this advantage to employ DNS tunneling as covert communication channel for C&C server. It’s very hard to differentiate the benign and malicious usage of DNS protocol for the traditional Firewall or IDS.
- Attacker registered a domain name hack.com. And its Name Server has pointed to the attacker’s C&C server where DNS Tunneling server program is installed. Since the Malware binary is hard coded with the domain name hack.com so all the DNS Query made by the malware will be forwarded to the attacker’s C&C server.
- The malware stole sensitive username and password data then sends those data as a DNS query to the Recursive DNS Server.
- The Recursive DNS Server tries to resolve the DNS query by checking its DNS cache but it cannot resolve the domain from its cache so it recursively forward the DNS query packet through the Firewall to the Root Server, TLD Server, finally the DNS query is routed to the attacker’s C&C Server (Name Server) where the DNS tunneling server program is running.
- Attacker track down DNS Queries with stolen data from server query log then decrypts the DNS Query and gets the username and password.
- Attacker’s Nameserver (C&C Server) sends back DNS Response with new command encoded into Resource Record (RR) back to the infected host.
That’s how botmaster can establish two way transactional communication channel using DNS Tunnel.
Upstream Payload Size (In DNS Query):
Fully Qualified Domain Name (FQDN) is formed with series of labels separated by periods. Basically FQDN has three part [Hostname].[Second-level Domain].[TLD] where the second-level domain might also include subdomain. FQDN also require a period at the end. e.g. label2.label1.domain.com.
DNS Tunnel utilizes the hostname label for upstream data. The amount of data that can be exfiltrated in each DNS Query packet is limited by the length of domain names. The maximum length of a FQDN is 255 characters including dots, with each label (subdomain) limited to 63 characters. The malware (Bot) uses maximum 63 characters in FQDN label to encode payload data within a DNS query.
Downstream Payload Size (In DNS Response):
DNS Tunnel utilizes various Resource Record (RR) for downstream data. The TXT record has the 255 octets limit for storing data in the RDATA field. The CNAME record has also limitation of 255 octets for data storage. And the NULL record allows 65535 octets. Besides these mostly used Resource Record, there are some other RR which is also used for DNS Tunneling. “Sending DNS packets over UDP are restricted to 512 bytes (not counting the IP or UDP headers)”, (RFC1035). To increase the payload size EDNS0 (Extension Mechanisms for DNS) can be used. An EDNS0 compatible server receiving a request from an EDNS0 compatible client may send UDP DNS packets over 512 Bytes limit.
DNS based covert Command-and-Control (C&C) channel is extremely robust, hard to detect and provide extra resilience and mobility to the C&C server. Botnets C&C communication over covert DNS Tunnel can be easily disguised as legitimate traffic and because DNS is always allowed in Firewall rules the malicious traffic can bypass the firewall easily. This makes the DNS Tunnel ideal for malwares covert communication channel and botmasters take advantage of DNS Tunnel to perform various malicious activities. Employing DNS Based C&C communications and rallying mechanism ensures attackers to mitigate takedown by removing single point of failure (SPOF). If one C&C server was taken down, attacker can set up another C&C server with a different IP address by updating DNS record. Domain Fluxing using DGA and implementation of Fast Flux makes it even more difficult for the security researcher to take down the C&C server.













Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.
You have Successfully Subscribed!