In today’s cybersecurity landscape, attackers are getting smarter and stealthier. Traditional malware that drops suspicious files on your disk is easier to spot and block. Enter Living off the Land (LotL) attacks, a technique where cybercriminals leverage your own trusted system tools to execute malicious code without leaving obvious traces. These fileless attacks run primarily in memory, blending seamlessly with legitimate operations and evading many antivirus solutions. If you’re a blue teamer or security analyst looking to understand how LotL works then this guide is for you.
What is Living off the Land (LotL)?
Living off the land (LotL) is an attack technique where adversaries abuse built in operating system components and management frameworks to run malicious code or commands. These components include native binaries, DLLs, script hosts, interpreters, configuration features, services, and protocols. The LotL aim is to use what the system already trusts so the malicious activity blends with normal operations and avoids attention. LotL often enables fileless execution where malware runs in memory and leaves little or no trace on disk.
What attackers abuse in LotL:
- LOLbins (native binaries): powershell.exe, mshta.exe, rundll32.exe, regsvr32.exe, certutil.exe, bitsadmin.exe, wscript.exe, cscript.exe, cmd.exe.
- Management frameworks: WMI, Task Scheduler.
- Scripts & libraries: LOLScript (e.g., PowerShell/VBScript/JScript run by trusted hosts) and LOLLib (DLLs loaded by trusted processes).
- Configuration & protocols: Registry Run keys, scheduled tasks, Group Policy, WinRM, administrative shares/services.
Using these tools and features, adversaries execute code in memory or launch small stagers that fetch and install larger payloads. They harvest credentials, move laterally, and establish persistence through scheduled tasks, Registry Run keys, services, or signed drivers. LotL activity can be fully fileless or leave only minimal disk artifacts, which makes detection harder.
The Standard LotL Attack Flow:
LotL attacks follow a structured progression, often aligning with frameworks like MITRE ATT&CK. Here’s the typical flow:
- Initial Access: Attacker gains a foothold via various vectors, such as exploiting vulnerabilities for remote code execution (RCE), phishing (e.g., malicious email attachments or links delivering scripts), compromised credentials (e.g., stolen via brute force or infostealers), supply chain attacks (e.g., tampered updates), or drive-by downloads from compromised websites.
- Post-exploitation with LoTL: Abuse trusted components (PowerShell, WMI, Task Scheduler, signed binaries) to escalate privileges, harvest creds, move laterally, and establish persistence (e.g., scheduled tasks, Registry Run keys).
- Low-artifact execution: Code often runs in memory or as scripts instead of new executables on disk, leaving fewer artifacts and mimicking admin behavior—harder to detect and respond.
PowerShell in LotL Attacks: A Fileless Execution Example
Attacker may use PowerShell to download and execute a malicious payload directly in memory instead of writing a new executable to disk.
powershell.exe -NoProfile -WindowStyle Hidden -EncodedCommand <payload>
Runs PowerShell with a Base64-encoded script passed on the command line; the decoded script typically downloads and executes code directly in memory. This lets an attacker run malicious logic without writing a new executable to disk, hide the console window from the user, and avoid loading profile scripts that might log or block the activity.
LOLBins (Living Off the Land Binaries) — objects/tools:
LOLBins are the specific legitimate executable programs (binaries) that attackers abuse in LotL attacks e.g., powershell.exe, rundll32.exe, certutil.exe, mshta.exe. These are normal, vendor-signed or built-in binaries that serve legitimate admin tasks but can also be misused by attackers. For example, certutil.exe is designed to manage certificates yet can be abused to download files (including malware), and powershell.exe is intended for automation and scripting but can run attacker-crafted scripts.
Any executables included in the OS that can be leveraged to carry out malicious actions are considered LOLBins. Similarly, user installed binaries may become LOLBins if they belong to common or popular third-party applications and can be misused.
Common LOLBins:
- Rundll32.exe: Loads DLLs for execution, often used to run malicious code in memory.
- Mshta.exe: Executes HTML applications, abused for running JavaScript or VBScript payloads.
- Regsvr32.exe: Registers DLLs, but can fetch and execute remote scripts.
- Cscript.exe/Wscript.exe: Script hosts for running JScript or VBScript.
- Cmstp.exe: Installs connection manager profiles, exploited for bypassing User Account Control (UAC).
- At.exe/Schtasks.exe: Schedules tasks for persistence or delayed execution.
Creating Fileless LotL with PowerShell and Detecting with Sysmon:
I’ll demonstrate three benign LotL examples to show how the LotL technique works from an adversary’s perspective. These examples are harmless and designed for blue-team learning and detection tuning. Run them in a disposable VM or lab network.
LotL Example 1: PowerShell File Creation – Dropping a Visible Disk Artifact
- Demonstrates a trusted binary (PowerShell) performing simple file I/O. This demonstrates a simple Living-off-the-Land (LoTL) action using built-in PowerShell to create C:\Temp and write hello.txt with the text “Hello World.” This is example is not fileless.
LotL Example 2: Fileless Network Persistence – Continuous Ping via Hidden cmd.exe
- This demonstrates Living off the Land (LotL): attacker uses built-in PowerShell to run an in-memory payload that starts cmd.exe to continuously ping 8.8.8.8. No files are written to disk.
LotL Example 3: In-Memory .NET Compilation – Benign Add-Type Payload Execution
- Demonstrate a fully fileless technique where PowerShell compiles and runs a tiny C# assembly entirely in memory. The assembly shows a MessageBox (“Hello from memory”) so we will have a visible confirmation. No files are written to disk.
LotL Example 1: PowerShell File Creation – Dropping a Visible Disk Artifact
This example creates a Temp folder on the C: drive and a file named hello.txt inside it containing the text “Hello World.”
Step 1: Main Payload Script (Harmless):
PowersShell Command:
New-Item -Path 'C:\Temp' -ItemType Directory -Force Add-Content -Path 'C:\Temp\hello.txt' -Value 'Hello World'
The “main payload script” is what we’ll execute using a LotL technique. This represents the action an attacker wants to perform. Next, we’ll encode it in Base64 (UTF-16LE) to obscure the plain-text command line.
Step 2: Create the Base64 (UTF-16LE) encoded string in PowerShell:
[Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes("New-Item -Path 'C:\Temp' -ItemType Directory -Force; Add-Content -Path 'C:\Temp\hello.txt' -Value 'Hello World'"))
Once you run the PowerShell command from Step 2, you should see an encoded string like:
Encoded (use with -EncodedCommand):
TgBlAHcALQBJAHQAZQBtACAALQBQAGEAdABoACAAJwBDADoAXABUAGUAbQBwACcAIAAtAEkAdABlAG0AVAB5AHAAZQAgAEQAaQByAGUAYwB0AG8AcgB5ACAALQBGAG8AcgBjAGUAOwAgAEEAZABkAC0AQwBvAG4AdABlAG4AdAAgAC0AUABhAHQAaAAgACcAQwA6AFwAVABlAG0AcABcAGgAZQBsAGwAbwAuAHQAeAB0ACcAIAAtAFYAYQBsAHUAZQAgACcASABlAGwAbABvACAAVwBvAHIAbABkACcA
Now our command is ready in base64 encoded string. We will use this encoded string as payload to our LoTL Invocation Template — PowerShell -EncodedCommand.
How to decode an -EncodedCommand value (PowerShell):
If you want to inspect the Base64 and see the original script:
$b64 = "<base64-string>" [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($b64))
LoTL Invocation Template — PowerShell -EncodedCommand:
powershell.exe -NoProfile -WindowStyle Hidden -EncodedCommand <payload>
-NoProfile: avoid loading profile scripts that might log/block.
-WindowStyle Hidden: hide console window (remove this flag for testing).
-EncodedCommand: executes a Base64-encoded UTF-16LE script.
Step 3: Execute the Encoded LotL PowerShell Command
Now we will just place the encoded string in our “PowerShell -EncodedCommand” <payload> section and run the command.
powershell.exe -NoProfile -WindowStyle Hidden -EncodedCommand TgBlAHcALQBJAHQAZQBtACAALQBQAGEAdABoACAAJwBDADoAXABUAGUAbQBwACcAIAAtAEkAdABlAG0AVAB5AHAAZQAgAEQAaQByAGUAYwB0AG8AcgB5ACAALQBGAG8AcgBjAGUAOwAgAEEAZABkAC0AQwBvAG4AdABlAG4AdAAgAC0AUABhAHQAaAAgACcAQwA6AFwAVABlAG0AcABcAGgAZQBsAGwAbwAuAHQAeAB0ACcAIAAtAFYAYQBsAHUAZQAgACcASABlAGwAbABvACAAVwBvAHIAbABkACcA
After running the command, we will observe that the powershell window will close immediately and there will be a folder Temp created in C: drive a file named hello.txt inside it containing the text “Hello World.”
The same thing can be achieved also by the non encoded command from step 1.
New-Item -Path 'C:\Temp' -ItemType Directory -Force Add-Content -Path 'C:\Temp\hello.txt' -Value 'Hello World'
And if we look at the Sysmon log we will see the event:
Process Create:
RuleName: -
UtcTime: 2025-10-02 17:17:06.725
ProcessGuid: {3a380209-b392-68de-3b03-000000003800}
ProcessId: 11200
Image: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
FileVersion: 10.0.19041.3996 (WinBuild.160101.0800)
Description: Windows PowerShell
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: PowerShell.EXE
CommandLine: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -WindowStyle Hidden -EncodedCommand TgBlAHcALQBJAHQAZQBtACAALQBQAGEAdABoACAAJwBDADoAXABUAGUAbQBwACcAIAAtAEkAdABlAG0AVAB5AHAAZQAgAEQAaQByAGUAYwB0AG8AcgB5ACAALQBGAG8AcgBjAGUAOwAgAEEAZABkAC0AQwBvAG4AdABlAG4AdAAgAC0AUABhAHQAaAAgACcAQwA6AFwAVABlAG0AcABcAGgAZQBsAGwAbwAuAHQAeAB0ACcAIAAtAFYAYQBsAHUAZQAgACcASABlAGwAbABvACAAVwBvAHIAbABkACcA
CurrentDirectory: C:\Users\admin\
User: SIEM2\admin
LogonGuid: {3a380209-8b5b-68de-312b-020000000000}
LogonId: 0x22B31
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=2E5A8590CF6848968FC23DE3FA1E25F1,SHA256=9785001B0DCF755EDDB8AF294A373C0B87B2498660F724E76C4D53F9C217C7A3,IMPHASH=3D08F4848535206D772DE145804FF4B6
ParentProcessGuid: {3a380209-b362-68de-3103-000000003800}
ParentProcessId: 10104
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentCommandLine: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
ParentUser: SIEM2\admin
Analyzing the Sysmon Log:
This log captures the child PowerShell process spawned by a parent PowerShell instance, a common LotL chaining tactic. Key red flags for detection tuning include: the -EncodedCommand parameter (indicating obfuscation), -WindowStyle Hidden (evasion attempt), and the absence of a RuleName (no existing rule fired—consider adding one for PowerShell with encoded args). The hashes and GUIDs can help baseline normal vs. anomalous invocations, while the medium integrity level suggests user-context execution without escalation.
LotL Example 2: Fileless Network Persistence – Continuous Ping via Hidden cmd.exe
This demonstrates Living off the Land (LotL): attacker uses built-in PowerShell to run an in-memory payload that starts cmd.exe to continuously ping 8.8.8.8. No files are written to disk.
Step 1: Plain script (PowerShell) — runs a short ping without writing to disk
This script uses PowerShell to start cmd.exe and run ping 8.8.8.8 -t. It does not write any files.
Start-Process -FilePath 'cmd.exe' -ArgumentList '/c ping 8.8.8.8 -t' -WindowStyle Hidden
Notes:
- Start-Process launches cmd.exe which will execute the ping.
- Nothing is saved to disk; the only artifacts are process creation and network traffic.
- -WindowStyle Hidden hides the console window; remove it for visible output.
Step 2: Create the Base64 (UTF-16LE) string (PowerShell)
To encode the above script into the format PowerShell expects for -EncodedCommand we can run either One-liner or Interactive steps PowerShell command.
One-liner:
[Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes("Start-Process -FilePath 'cmd.exe' -ArgumentList '/c ping 8.8.8.8 -t' -WindowStyle Hidden"))
Interactive steps:
$script = "Start-Process -FilePath 'cmd.exe' -ArgumentList '/c ping 8.8.8.8 -t' -WindowStyle Hidden" $bytes = [System.Text.Encoding]::Unicode.GetBytes($script) $b64 = [Convert]::ToBase64String($bytes) $b64
Encoded String Output:
UwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgAC0ARgBpAGwAZQBQAGEAdABoACAAJwBjAG0AZAAuAGUAeABlACcAIAAtAEEAcgBnAHUAbQBlAG4AdABMAGkAcwB0ACAAJwAvAGMAIABwAGkAbgBnACAAOAAuADgALgA4AC4AOAAgAC0AdAAnACAALQBXAGkAbgBkAG8AdwBTAHQAeQBsAGUAIABIAGkAZABkAGUAbgA=
Step 3: Final LotL PowerShell Full Command:
powershell.exe -NoProfile -WindowStyle Hidden -EncodedCommand UwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgAC0ARgBpAGwAZQBQAGEAdABoACAAJwBjAG0AZAAuAGUAeABlACcAIAAtAEEAcgBnAHUAbQBlAG4AdABMAGkAcwB0ACAAJwAvAGMAIABwAGkAbgBnACAAOAAuADgALgA4AC4AOAAgAC0AdAAnACAALQBXAGkAbgBkAG8AdwBTAHQAeQBsAGUAIABIAGkAZABkAGUAbgA=
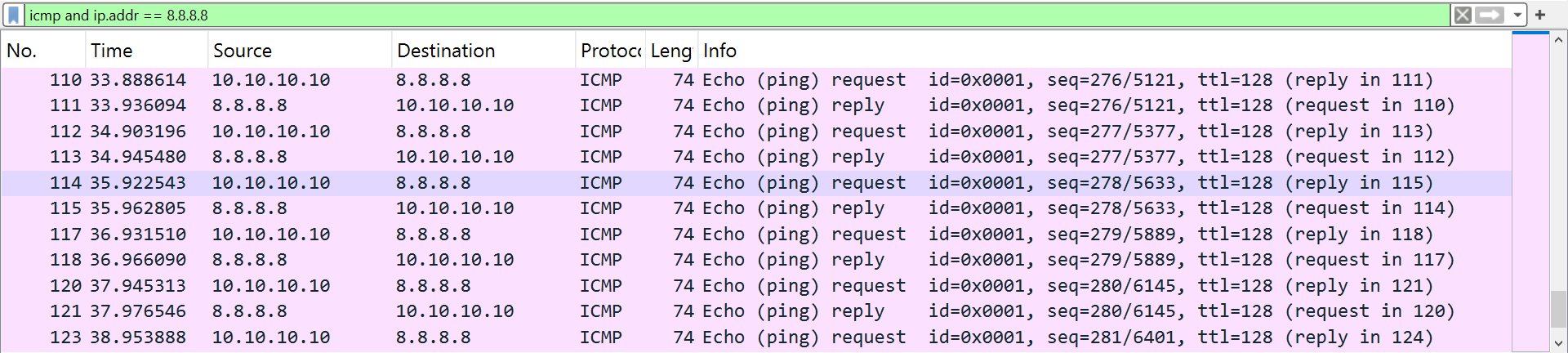
When you run this command from PowerShell, the console window closes immediately with no visible output. In the background, however, a cmd.exe process continuously pings 8.8.8.8. You can confirm this with Process Hacker or System Informer. You can also use Wireshark to monitor ICMP packets you’ll see the ping traffic.
Process Tracking (System Informer):
- Open System Informer (Run as Administrator).
- Search for “cmd” in the search bar.
- After launching the hidden PowerShell command, a new cmd.exe process will appear.
- Track down the cmd.exe process; it will show a ping.exe process running as its child.
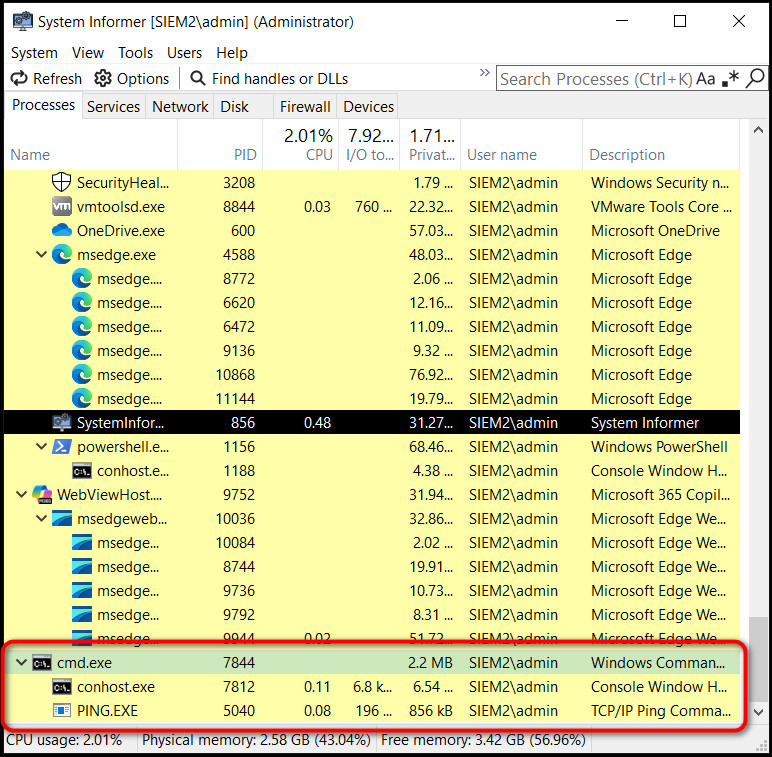
Network Monitoring (Wireshark):
- Open Wireshark.
- Set the Display Filter to show the specific ICMP traffic: icmp and ip.addr == 8.8.8.8
- Start monitoring.
- You will see a continuous stream of ICMP packets confirming the ping to 8.8.8.8.
Sysmon Event For cmd.exe:
Process Create:
RuleName: -
UtcTime: 2025-10-02 18:22:51.608
ProcessGuid: {3a380209-c2fb-68de-7e01-000000003900}
ProcessId: 7844
Image: C:\Windows\System32\cmd.exe
FileVersion: 10.0.19041.4355 (WinBuild.160101.0800)
Description: Windows Command Processor
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: Cmd.Exe
CommandLine: "C:\Windows\system32\cmd.exe" /c ping 8.8.8.8 -t
CurrentDirectory: C:\Users\admin\
User: SIEM2\admin
LogonGuid: {3a380209-c277-68de-060e-020000000000}
LogonId: 0x20E06
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=2B40C98ED0F7A1D3B091A3E8353132DC,SHA256=BADF4752413CB0CBDC03FB95820CA167F0CDC63B597CCDB5EF43111180E088B0,IMPHASH=272245E2988E1E430500B852C4FB5E18
ParentProcessGuid: {3a380209-c2fa-68de-7d01-000000003900}
ParentProcessId: 7640
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentCommandLine: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -WindowStyle Hidden -EncodedCommand UwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgAC0ARgBpAGwAZQBQAGEAdABoACAAJwBjAG0AZAAuAGUAeABlACcAIAAtAEEAcgBnAHUAbQBlAG4AdABMAGkAcwB0ACAAJwAvAGMAIABwAGkAbgBnACAAOAAuADgALgA4AC4AOAAgAC0AdAAnACAALQBXAGkAbgBkAG8AdwBTAHQAeQBsAGUAIABIAGkAZABkAGUAbgA=
ParentUser: SIEM2\admin
Sysmon Event for ping.exe :
Process Create:
RuleName: -
UtcTime: 2025-10-02 18:22:51.716
ProcessGuid: {3a380209-c2fb-68de-8001-000000003900}
ProcessId: 5040
Image: C:\Windows\System32\PING.EXE
FileVersion: 10.0.19041.1 (WinBuild.160101.0800)
Description: TCP/IP Ping Command
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: ping.exe
CommandLine: ping 8.8.8.8 -t
CurrentDirectory: C:\Users\admin\
User: SIEM2\admin
LogonGuid: {3a380209-c277-68de-060e-020000000000}
LogonId: 0x20E06
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=2F46799D79D22AC72C241EC0322B011D,SHA256=7AF50FA112932EA3284F7821B2EEA2B7582F558DBA897231BB82182003C29F8B,IMPHASH=8C3BE1286CDAD6AC1136D0BB6C83FF41
ParentProcessGuid: {3a380209-c2fb-68de-7e01-000000003900}
ParentProcessId: 7844
ParentImage: C:\Windows\System32\cmd.exe
ParentCommandLine: "C:\Windows\system32\cmd.exe" /c ping 8.8.8.8 -t
ParentUser: SIEM2\admin
Sysmon Analysis:
By analyzing these logs, we can see PowerShell (PID 7640) spawns cmd.exe (PID 7844) via a hidden/encoded command for fileless evasion, then cmd.exe launches PING.EXE (PID 5040) to run continuous ping 8.8.8.8 -t, linked by parent-child PID relations for stealthy persistence. No RuleName fired, signaling untuned rules—tune Sigma alerts for encoded PowerShell → cmd → ping chains, correlating with Wireshark ICMP traffic for detection. Hashes/GUIDs baseline legit binaries, but the obfuscated tree flags anomalies.
Step 4: Termination
To stop the continuous ping action, terminate the child ping.exe process shown under the cmd.exe parent process in System Informer.
Now let’s view the cmd.exe output by removing the -WindowStyle Hidden flag and running the same command again. This time, you’ll see the ping in the console.
Visible console (remove hidden flag to watch output):
powershell.exe -NoProfile -EncodedCommand UwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgAC0ARgBpAGwAZQBQAGEAdABoACAAJwBjAG0AZAAuAGUAeABlACcAIAAtAEEAcgBnAHUAbQBlAG4AdABMAGkAcwB0ACAAJwAvAGMAIABwAGkAbgBnACAAOAAuADgALgA4AC4AOAAgAC0AdAAnAA==
LotL Example 3: In-Memory .NET Compilation – Benign Add-Type Payload Execution
Demonstrate a fully fileless technique where PowerShell compiles and runs a tiny C# assembly entirely in memory. The assembly shows a MessageBox (“Hello from memory”) so we can have a visible confirmation. No files are written to disk.
Step 1: Plain PowerShell Script – The in-memory payload (Benign)
This compiles a tiny C# class into an in-memory assembly via Add-Type and invokes a method that shows a MessageBox. Nothing is written to disk.
$source = @"
using System.Windows.Forms;
public class HelloWorld {
public static void Say() {
MessageBox.Show("Hello from memory","In-Memory Demo");
}
}
"@
Add-Type -TypeDefinition $source -ReferencedAssemblies System.Windows.Forms
[HelloWorld]::Say()
Notes
- Add-Type -TypeDefinition compiles the C# source into an in-memory assembly (no DLL dropped to disk).
- The MessageBox provides a visible, unmistakable indicator.
- This is benign: it only demonstrates loading and running a managed assembly entirely in memory.
Step 2: Create the Base64 (UTF-16LE) String
Prepare the script for use with -EncodedCommand.
Interactive encoding:
$script = '<paste the script text exactly as above>' $bytes = [System.Text.Encoding]::Unicode.GetBytes($script) $b64 = [Convert]::ToBase64String($bytes) $b64 # copy this value for -EncodedCommand
Example Command:
$script = '$source = @"
using System.Windows.Forms;
public class HelloWorld {
public static void Say() {
MessageBox.Show("Hello from memory","In-Memory Demo");
}
}
"@
Add-Type -TypeDefinition $source -ReferencedAssemblies System.Windows.Forms
[HelloWorld]::Say()
'
$bytes = [System.Text.Encoding]::Unicode.GetBytes($script)
$b64 = [Convert]::ToBase64String($bytes)
$b64 # copy this value for -EncodedCommandStep 3: Encoded string (ready to use)
JABzAG8AdQByAGMAZQAgAD0AIABAACIACgB1AHMAaQBuAGcAIABTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMAOwAKAHAAdQBiAGwAaQBjACAAYwBsAGEAcwBzACAASABlAGwAbABvAFcAbwByAGwAZAAgAHsACgAgACAAcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAHYAbwBpAGQAIABTAGEAeQAoACkAIAB7AAoAIAAgACAAIABNAGUAcwBzAGEAZwBlAEIAbwB4AC4AUwBoAG8AdwAoACIASABlAGwAbABvACAAZgByAG8AbQAgAG0AZQBtAG8AcgB5ACIALAAiAEkAbgAtAE0AZQBtAG8AcgB5ACAARABlAG0AbwAiACkAOwAKACAAIAB9AAoAfQAKACIAQAAgAAoAQQBkAGQALQBUAHkAcABlACAALQBUAHkAcABlAEQAZQBmAGkAbgBpAHQAaQBvAG4AIAAkAHMAbwB1AHIAYwBlACAALQBSAGUAZgBlAHIAZQBuAGMAZQBkAEEAcwBzAGUAbQBiAGwAaQBlAHMAIABTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMACgBbAEgAZQBsAGwAbwBXAG8AcgBsAGQAXQA6ADoAUwBhAHkAKAApAAoA
Step 4: LotL In-memory .NET payload Full Command to Run (Hidden Console):
Before running, open Process Hacker or System Informer.
Search for powershell.exe.
When executing the full command, a new powershell.exe process with a new PID appears. In my case new PID was 468.
A MessageBox pops up: In-Memory Demo → Hello from memory.
powershell.exe -NoProfile -WindowStyle Hidden -EncodedCommand JABzAG8AdQByAGMAZQAgAD0AIABAACIACgB1AHMAaQBuAGcAIABTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMAOwAKAHAAdQBiAGwAaQBjACAAYwBsAGEAcwBzACAASABlAGwAbABvAFcAbwByAGwAZAAgAHsACgAgACAAcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAHYAbwBpAGQAIABTAGEAeQAoACkAIAB7AAoAIAAgACAAIABNAGUAcwBzAGEAZwBlAEIAbwB4AC4AUwBoAG8AdwAoACIASABlAGwAbABvACAAZgByAG8AbQAgAG0AZQBtAG8AcgB5ACIALAAiAEkAbgAtAE0AZQBtAG8AcgB5ACAARABlAG0AbwAiACkAOwAKACAAIAB9AAoAfQAKACIAQAAgAAoAQQBkAGQALQBUAHkAcABlACAALQBUAHkAcABlAEQAZQBmAGkAbgBpAHQAaQBvAG4AIAAkAHMAbwB1AHIAYwBlACAALQBSAGUAZgBlAHIAZQBuAGMAZQBkAEEAcwBzAGUAbQBiAGwAaQBlAHMAIABTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMACgBbAEgAZQBsAGwAbwBXAG8AcgBsAGQAXQA6ADoAUwBhAHkAKAApAAoA
In my case, Powershell PID was 468
Sysmon Event Log:
EID 1 — PowerShell launched (PID 468) with -EncodedCommand & Hidden window
Process Create:
RuleName: -
UtcTime: 2025-10-02 19:31:27.847
ProcessGuid: {3a380209-d30f-68de-4202-000000003900}
ProcessId: 468
Image: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
FileVersion: 10.0.19041.3996 (WinBuild.160101.0800)
Description: Windows PowerShell
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: PowerShell.EXE
CommandLine: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -WindowStyle Hidden -EncodedCommand JABzAG8AdQByAGMAZQAgAD0AIABAACIACgB1AHMAaQBuAGcAIABTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMAOwAKAHAAdQBiAGwAaQBjACAAYwBsAGEAcwBzACAASABlAGwAbABvAFcAbwByAGwAZAAgAHsACgAgACAAcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAHYAbwBpAGQAIABTAGEAeQAoACkAIAB7AAoAIAAgACAAIABNAGUAcwBzAGEAZwBlAEIAbwB4AC4AUwBoAG8AdwAoACIASABlAGwAbABvACAAZgByAG8AbQAgAG0AZQBtAG8AcgB5ACIALAAiAEkAbgAtAE0AZQBtAG8AcgB5ACAARABlAG0AbwAiACkAOwAKACAAIAB9AAoAfQAKACIAQAAgAAoAQQBkAGQALQBUAHkAcABlACAALQBUAHkAcABlAEQAZQBmAGkAbgBpAHQAaQBvAG4AIAAkAHMAbwB1AHIAYwBlACAALQBSAGUAZgBlAHIAZQBuAGMAZQBkAEEAcwBzAGUAbQBiAGwAaQBlAHMAIABTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMACgBbAEgAZQBsAGwAbwBXAG8AcgBsAGQAXQA6ADoAUwBhAHkAKAApAAoA
CurrentDirectory: C:\Users\admin\
User: SIEM2\admin
LogonGuid: {3a380209-c277-68de-060e-020000000000}
LogonId: 0x20E06
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=2E5A8590CF6848968FC23DE3FA1E25F1,SHA256=9785001B0DCF755EDDB8AF294A373C0B87B2498660F724E76C4D53F9C217C7A3,IMPHASH=3D08F4848535206D772DE145804FF4B6
ParentProcessGuid: {3a380209-d2cf-68de-3f02-000000003900}
ParentProcessId: 5284
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentCommandLine: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
ParentUser: SIEM2\admin
Sysmon Event Log:
EID 1 — csc.exe spawned by PowerShell (Add-Type compile step)
Process Create:
RuleName: -
UtcTime: 2025-10-02 19:31:28.260
ProcessGuid: {3a380209-d310-68de-4302-000000003900}
ProcessId: 4428
Image: C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe
FileVersion: 4.8.9232.0 built by: NET481REL1LAST_C
Description: Visual C# Command Line Compiler
Product: Microsoft® .NET Framework
Company: Microsoft Corporation
OriginalFileName: csc.exe
CommandLine: "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\jwpwrxaj.cmdline"
CurrentDirectory: C:\Users\admin\
User: SIEM2\admin
LogonGuid: {3a380209-c277-68de-060e-020000000000}
LogonId: 0x20E06
TerminalSessionId: 1
IntegrityLevel: Medium
Hashes: MD5=53803CB67327CC873A1C88604D54A1D4,SHA256=AAE1DB57F898CA8BDA18590C56F86CED6D0EAD80C22033B76FDFE9119706F116,IMPHASH=2E6A9097FBA347A254DAC72662FE1259
ParentProcessGuid: {3a380209-d30f-68de-4202-000000003900}
ParentProcessId: 468
ParentImage: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ParentCommandLine: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -WindowStyle Hidden -EncodedCommand JABzAG8AdQByAGMAZQAgAD0AIABAACIACgB1AHMAaQBuAGcAIABTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMAOwAKAHAAdQBiAGwAaQBjACAAYwBsAGEAcwBzACAASABlAGwAbABvAFcAbwByAGwAZAAgAHsACgAgACAAcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAHYAbwBpAGQAIABTAGEAeQAoACkAIAB7AAoAIAAgACAAIABNAGUAcwBzAGEAZwBlAEIAbwB4AC4AUwBoAG8AdwAoACIASABlAGwAbABvACAAZgByAG8AbQAgAG0AZQBtAG8AcgB5ACIALAAiAEkAbgAtAE0AZQBtAG8AcgB5ACAARABlAG0AbwAiACkAOwAKACAAIAB9AAoAfQAKACIAQAAgAAoAQQBkAGQALQBUAHkAcABlACAALQBUAHkAcABlAEQAZQBmAGkAbgBpAHQAaQBvAG4AIAAkAHMAbwB1AHIAYwBlACAALQBSAGUAZgBlAHIAZQBuAGMAZQBkAEEAcwBzAGUAbQBiAGwAaQBlAHMAIABTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMACgBbAEgAZQBsAGwAbwBXAG8AcgBsAGQAXQA6ADoAUwBhAHkAKAApAAoA
ParentUser: SIEM2\admin
Sysmon Event Log:
Sysmon Log (Event ID 7: Image Loaded)
EID 7 — clrjit.dll loaded in PowerShell (CLR JIT engaged for managed code)
Image loaded:
RuleName: -
UtcTime: 2025-10-02 19:31:27.974
ProcessGuid: {3a380209-d30f-68de-4202-000000003900}
ProcessId: 468
Image: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
ImageLoaded: C:\Windows\Microsoft.NET\Framework64\v4.0.30319\clrjit.dll
FileVersion: 4.8.9310.0 built by: NET481REL1LAST_C
Description: Microsoft .NET Runtime Just-In-Time Compiler
Product: Microsoft® .NET Framework
Company: Microsoft Corporation
OriginalFileName: clrjit.dll
Hashes: MD5=6C1E4C94862BFEC94F9F5F73D5D84554,SHA256=24FCAF2398115D6946E93739FCEB11B07D5D31C6B906B4F42A8037A5DB473D85,IMPHASH=F2AFE1578B0645F42EFCA5A3FB0CE765
Signed: true
Signature: Microsoft Corporation
SignatureStatus: Valid
User: SIEM2\admin
Sysmon Analysis:
These logs reveal a sophisticated in-memory .NET execution chain, highlighting LotL’s stealth via trusted binaries. The first Event ID 1 shows the initial powershell.exe spawn (PID 468) with -EncodedCommand and -WindowStyle Hidden, mirroring common obfuscation tactics—flag this for rules on hidden/encoded PowerShell launches. The second Event ID 1 captures the child csc.exe (C# compiler, PID 4428) invoked by PowerShell, using a temp file (jwpwrxaj.cmdline) for args; this is a strong indicator of dynamic compilation, rare in benign scripts—tune detections for PowerShell spawning csc.exe outside dev contexts. The Event ID 7 logs clrjit.dll loading in PowerShell, signaling JIT compilation for managed code; correlate this with the prior events to detect in-memory assembly creation. Overall, no RuleName means untuned rules—consider Sigma rules for PowerShell → csc.exe parent-child, JIT loads, and medium integrity .NET activity. Hashes/GUIDs aid baselining anomalous patterns.
References:
1. https://www.crowdstrike.com/en-us/cybersecurity-101/cyberattacks/living-off-the-land-attack/
2. https://www.paloaltonetworks.com/cyberpedia/what-are-fileless-malware-attacks
3. https://www.cisa.gov/resources-tools/resources/identifying-and-mitigating-living-land-techniques
4. https://www.fortinet.com/resources/cyberglossary/living-off-the-land-lotl
5. https://docs.broadcom.com/docs/istr-living-off-the-land-and-fileless-attack-techniques-en
6. https://techzone.bitdefender.com/en/tech-explainers/living-of-the-land-attacks.html
7. https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-Release-View/Article/3669159/combatting-cyber-threat-actors-perpetrating-living-off-the-land-intrusions/














Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.
You have Successfully Subscribed!